Executive Summary
The modern ransomware ecosystem has a terrifying truth: human agony is the ultimate liquidity. Operating through, "as-a-service" structures, loose networks of affiliates have transitioned from simple data theft to a systemic assault. These predators have transformed hospitals from sanctuaries of healing into hostage cells, betting that the desperation to save a life will always outweigh a hospital's digital defenses. This is no longer mere cybercrime; it is a collapse of ethical restraint that treats the cries of families as a bargaining advantage, effectively poisoning our world with a cold and digital cruelty.
The real-world consequences of this were recently mirrored at Kettering Health, where an attack by the Interlock group paralyzed medical centers across the system. While the health system fought to bring critical radiation oncology services back online, the incident exposed a reality: the life-sustaining treatments of thousands were held hostage for a payday. When imaging, labs, and pharmacies go dark, clinicians are forced to operate in a vacuum, delaying life-saving surgeries and diverting emergency care. This instability proves that patient safety now hangs by a thin thread—the whim of a faceless attacker. Whether a pediatric ward is spared or a cancer patient's treatment is halted depends entirely on the volatile and emotional distance of a person behind a screen.
This virus has branched far beyond the bedside, spreading into a global epidemic that threatens modern life. Ransomware is now a weapon aimed at the heart of our critical infrastructure, crippling the energy grids, supply chains, and financial systems that allow society to function. We have reached a point where our essential services—from the power in our homes to the food on our shelves—are reliable only until a predator decides otherwise. The targeting of these vital nerves represents a shift from financial extortion to a broad-scale assault on human rights and national security.
To end this cycle, the defense of our world must evolve from a reactive posture to a proactive, disruptive posture. We cannot simply build higher walls; we must engage in cybersecurity research that allows us to become the "wolf in sheep's clothing." Securing our future requires a unified front of innovation and policy to secure a world that belongs to us and not the extortionists.
This report introduces SHADOW, an ethical and reproducible workflow designed for the safe observation of ransomware affiliates. By utilizing synthetic personas, tactical empathy, and rigorous Operational Security (OPSEC), researchers can gain deep insights into threat actor behaviors without direct operational engagement or legal risk.
SHADOW stands for the following items. (S – Synthetic Identity, H – Human Engagement, A – Actor Mapping, D – Deep Observation, O – Operational Security and W – Weighting Intelligence).
| Acronym Letter | Full Concept | Description / Focus |
|---|---|---|
| S | Synthetic Identity | Creating or identifying non-existent/fabricated identities. |
| H | Human Engagement | Interaction with individuals, possibly for intelligence gathering or influence. |
| A | Actor Mapping | Identifying, documenting, and linking all involved parties or entities. |
| D | Deep Observation | In-depth, sustained, and detailed monitoring of targets or activities. |
| O | Operational Security | Protecting operations from detection or compromise by the adversary. |
| W | Weighting Intelligence | Assessing the reliability, relevance, and importance of collected information. |
Evaluation and ranking of collected intelligence based on credibility, corroboration, and relevance to investigative objectives. The report leverages real-world scenarios and the following items:
- Several composite cases built from research patterns
- Known behaviors and recruitment structures
- Generalizable Tactics, Techniques, & Procedures (TTPs) seen across groups
- High level infrastructure linking heuristics that avoid attribution risk
The goal is to provide a safe blueprint for researchers to generate actionable insights without exposure or identification.
The key to SHADOW HUMINT-style research:
- Every persona must be synthetic: The core principle is the creation of a completely fabricated digital and real-world identity (a "synthetic identity") that is not linked to the operator's true self or any other operation.
- Never reuse any ID (TOX, or XMPP, etc.): This is a critical security measure to prevent "cross-contamination" or the linking of different operations. Using a fresh communication identifier (like a TOX ID or XMPP account) for each task or target ensures that if one persona is compromised, others remain secure.
- Maintain a plausible, safe backstory: The synthetic persona needs a credible history and context that can withstand scrutiny. This backstory must be safe, meaning it doesn't accidentally reveal real-world connections or put the operator in danger.
- Use tactical empathy — understand motivations without engaging: This principle, drawn from negotiation and intelligence techniques, involves actively seeking to understand the target's emotions and perspective, but without revealing one's own agenda or engaging emotionally. The goal is to build a degree of rapport that encourages information sharing, not genuine connection.
- Maintain a listening-first posture: This means prioritizing active listening and information gathering over talking or giving opinions. The operator's role is to absorb information, not to direct the conversation or debate. This makes the target feel heard and encourages them to divulge more information naturally.
- Never provide or request actionable operational guidance. This rule ensures the work stays strictly intelligence-based, and non-operational, preventing it from being used to enable real attacks.
Example Synthetic identity:

Image source: https://this-person-does-not-exist.com
Persona: Elias "Nullkey" Ivanov. Age / Origin: 28, born in Yerevan, Armenia (CIS country).
Handle: Nullkey — chosen because he liked the idea of being "the missing key" in a system.
Education (English-only reason):
Elias attended the QSI International School of Yerevan, where all instruction was in English and most of his classmates were children of diplomats, NGO workers, or expats.
- His first exposure to computers came from the school's IT lab, which ran English-language software.
- Because all his classes, textbooks, and even after-school clubs were in English, he grew up thinking and working in it.
- Online, he never used Armenian or Russian — he stuck to English forums and chatrooms because it felt natural.
Backstory:
Elias grew up fascinated by computers his father repaired in their small apartment. When his family couldn't afford newer software, he learned to modify and repurpose older systems. By 16, he was hanging out in global IRC channels, speaking only English, and experimenting with code snippets he found online.
He went on to study computer engineering at the National Polytechnic University of Armenia, but dropped out after one year, preferring to learn by building tools and competing in capture-the-flag competitions. His English fluency meant he could read the newest research papers and talk to international peers without barriers.
Current role / lifestyle:
Lives modestly in Yerevan, freelancing as a security tester for companies abroad. He's known for publishing detailed write-ups (always in English) that gain traction in the global infosec community. Offline, he's quiet, but online he's active, witty, and sometimes sarcastic.
A synthetic identity is the analyst's primary defensive and offensive tool. When built with creativity and maintained with absolute belief, it becomes a digital mask that allows the researcher to stand in the same digital room as the enemy, invisible and uncompromised.
OPSEC Principles & Tactical Foundations
Operational Security (OPSEC) is the bedrock of the SHADOW framework. Analysts must attempt to maintain a "zero-leak" policy to ensure the safety of the research and the integrity of the synthetic persona.
I. Technical Isolation & Environment Security
To prevent the leakage of real-world identifiers, analysts must operate within a strictly siloed environment:
- Operating Systems: Use Tails or Whonix via Live USB to ensure a non-persistent, amnesic environment that leaves no trace on the local hardware.
- Traffic Routing: Utilize Torsocks to reroute all command-line application traffic over the Tor network or a secure SOCKS5 proxy.
- Sandboxing: Employ Firejail to restrict the running environment of untrusted applications, utilizing Linux namespaces and seccomp-bpf to mitigate the risk of a security breach.
- Data Handling:
- Secure Storage: Use dedicated, encrypted file storage for all evidence gathering.
- Secure Sharing: Use temporary, privacy-focused platforms like OnionShare or temp.sh for data transfer.
- Offline Logging: Record all notes and logs offline using tools like Obsidian, Notepad++, or CherryTree to prevent inadvertent cloud syncing or data leaks.
II. Behavioral Competency: The Human Element
Technical tools protect your IP, but your communication style protects your persona. Mastering emotional intelligence (EQ) is critical for safe and effective engagement.
- Effective Listening & Tactical Empathy: These are not just soft skills; they are intelligence tools used to increase cooperation and reveal hidden insights.
- Strategic Study: Analysts should be well-versed in behavioral psychology and negotiation tactics. Key foundational texts include:
- Surrounded by Idiots by Thomas Erikson: For understanding the four types of human behavior and adapting communication styles in real-time.
- Never Split the Difference by Chris Voss: For applying high-stakes negotiation tactics and tactical empathy to professional information gathering.
The "Living Lab": Learning from Public Interpersonal Dynamics
To understand Tactical Empathy and Effective Listening, analysts can gain insights by observing real-world interactions in popular media. Programs that feature negotiation, vetting, and deep emotional rapport provide a "living lab" to study how people react under pressure, how they value assets, and how they build or sometimes break trust.
The Art of the Deal: Pawn Stars & Hardcore Pawn
These shows are masterclasses in high-stakes negotiation and reading "tells."
- The Takeaway: Watch how the buyers use silence and "The Accusation Audit" to lower the seller's expectations. Notice the emotional shift when a seller is told their item is worth less than they thought—this mirrors how a ransomware operator might react when their "product" or "access" is questioned.
- Key Skill: Identifying the difference between a person's position (what they say they want) and their interest (the underlying need driving them).
Vetting and Power Dynamics: Shark Tank
Shark Tank mirrors the Ransomware-as-a-Service (RaaS) onboarding process. The "Sharks" are the operators, and the entrepreneurs are the potential affiliates.
- The Takeaway: Pay attention to how the Sharks vet an individual's character and technical knowledge within minutes. They look for confidence, consistency, and a "proven track record."
- Key Skill: Learning how to pitch a "synthetic persona" effectively and understanding what a high-level operator looks for in a partner.
Rapport and Radical Empathy: The Oprah Winfrey Show
Oprah is arguably one of the most successful practitioners of active listening and rapport building in modern media.
- The Takeaway: Observe how she uses open-ended questions and mirrors the guest's emotions to make them feel safe enough to reveal deeply personal information.
- Key Skill: Mastering the "O" (Observation) and "W" (Willingness to Engage) in the SHADOW framework. By making the adversary feel heard and understood, you lower their psychological "firewalls."
Safety is achieved through the complete separation of personal identity and research personas. By combining dedicated systems and network paths with disciplined behavioral techniques, an analyst can safely navigate the most dangerous corners of the dark web.
The Analyst's Operational Mindset
The effectiveness of any Cyber-HUMINT operation is fundamentally tied to the discipline of the analyst. Engaging with threat actors requires a specialized mindset that balances extreme curiosity with absolute discretion.
1. The Shield of Silence (OPSEC)
In the world of intelligence, information that is made public is information that is "burned." Public disclosure is often a self-inflicted wound to a long-term investigation.
Preventing "Intelligence Burn":
- The Scenario: An analyst discovers a new Command and Control (C2) server or a specific Tox ID used by a lead negotiator. In an effort to be the "first to report," they post the IP address and screenshots on X (Twitter).
- The Result: Threat actors monitor social media. Within minutes of the post, the actor wipes the server, rotates their encryption keys, and abandons that Tox ID. The analyst has just "tipped the hand" of the entire research community, effectively killing the lead.
Protecting the Personal Circle:
- The Scenario: An analyst uses their real-world handle or shares enough personal detail to be "doxed" by a disgruntled ransomware operator they were engaging.
- The Result: These groups are criminal syndicates. They have been known to engage in "Swatting" (sending emergency services to a home under false pretenses) or targeting an analyst's family members with harassment. Silence is the physical barrier between your work life and your home life.
2. Strategic Reporting & "Sealing" Data
Intelligence is only valuable if it leads to disruption or victim recovery. This requires a strict "Chain of Custody" for your findings to ensure they remain legally and operationally viable.
Official Communication Channels:
- The Scenario: During a Tox conversation, the operator provides a Bitcoin wallet address for a "test payment."
- The Action: Instead of posting it on a public tracker, the analyst immediately packages the wallet address, the timestamp, and the chat logs into a ZIP file and submits it to the FBI's IC3 portal.
- The Value: This allows Law Enforcement to coordinate with exchanges to freeze those funds or track the "money mule" behind the account.
Sealing the Intel:
- The Scenario: You identify a vulnerability in a group's new encryptor that could allow victims to recover files for free.
- The Action: You "seal" this information, sharing it only with CISA and trusted incident response partners.
The Result:
By not making this public, the threat actor doesn't realize their "product" is broken. This allows authorities to help dozens of victims quietly recover their data before the group can patch the flaw. If it were public, the group would fix the bug instantly, and future victims would be left without a solution.
3. Operational Persistence & The "Long Game"
Cyber-HUMINT is NOT a sprint; it is an endurance sport. An operational mindset requires the patience to let an actor feel safe and secure.
The Value of Inaction
- The Concept: Sometimes, the most professional thing an analyst can do is nothing.
- The Scenario: You gain access to a private "inner circle" chat room. Your instinct is to immediately scrape everything and report it.
- The Strategy: If you scrape too aggressively or ask too many questions too fast, you trigger "Security Paranoia" in the group.
- The Result: By staying quiet and only observing for weeks or months, you map the relationships and hierarchies, which is far more valuable than a single leaked IP address.
Comparison of Mindsets: Reactive vs. Operational
| Feature | Reactive Analyst (High Risk) | Operational Analyst (SHADOW) |
|---|---|---|
| Primary Goal | Social Media "Clout" / Immediate "Wins" | Long-term Disruption / Attribution |
| Communication | Public (X, Blogs, GitHub) | Protected (LEO, TLP:RED circles) |
| Response to Data | Posts immediately to "burn" the actor | Seeds data for law enforcement "takedowns" |
| Perspective | Sees a "Criminal" to be mocked | Sees an "Intelligence Target" to be mapped |
In the example below, an analyst chooses public platforms (like X) to "call out" a threat actor for poor OpSec and transition from an Intelligence Asset to a Target. The adoption of an operational mindset is what separates a hobbyist from a professional intelligence practitioner. In the high-stakes environment of Cyber-HUMINT, the impulse to share and the desire for immediate recognition are the analyst's greatest vulnerabilities.
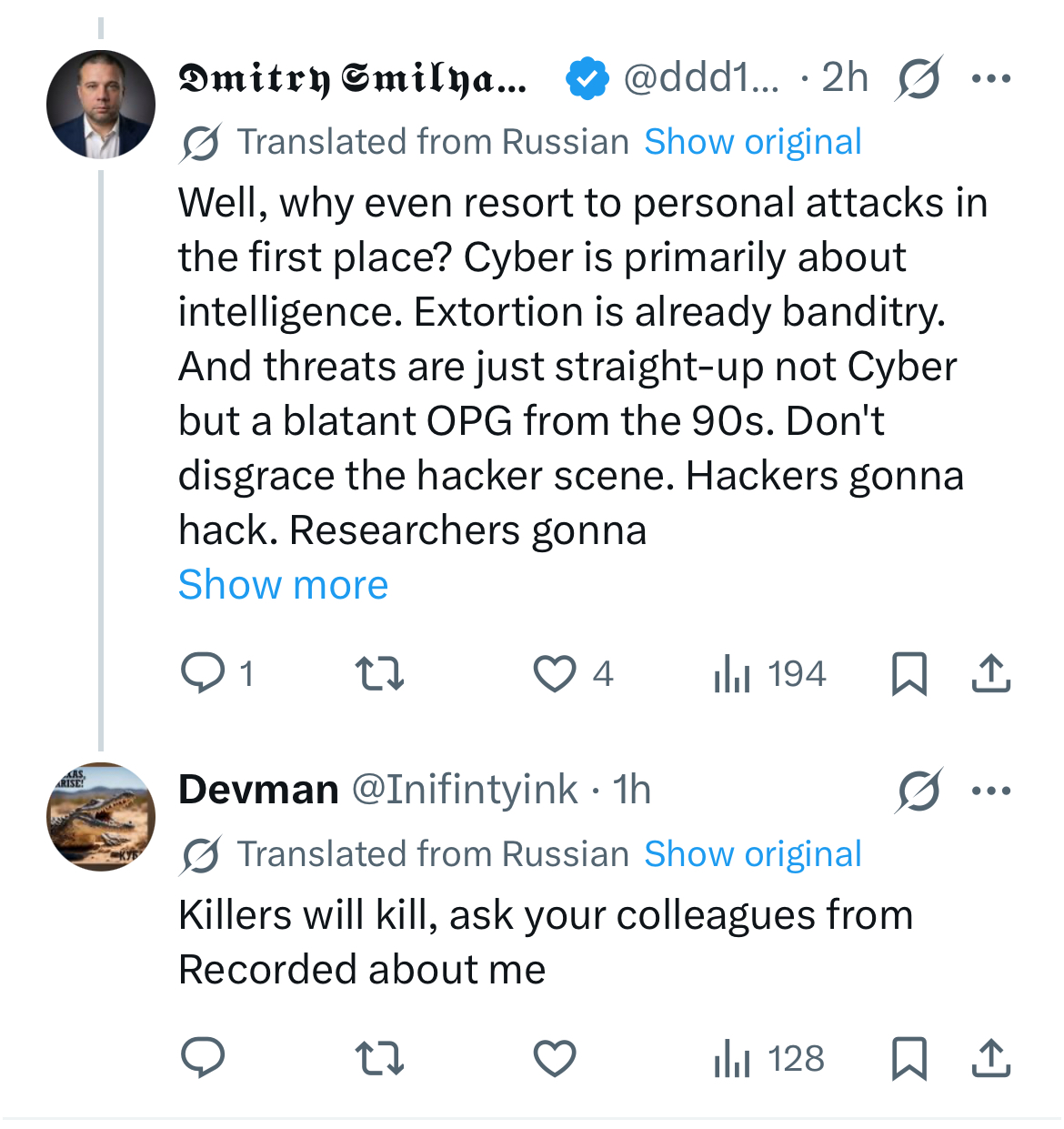
Exchange between ransomware actor and researcher on X.
Ultimately, the SHADOW framework is designed to ensure that the analyst remains a ghost in the machine and effective at threat intelligence gathering. By mastering the operational mindset, the analyst ensures that their work doesn't just create "noise" on social media, but creates consequences for threat actors in the physical world. It's the only way cybersecurity researchers can make a difference.
RaaS in Small Groups
Ransomware-as-a-Service (RaaS) thrives in smaller or emerging crews because it gives them instant infrastructure, tooling, and support they otherwise wouldn't have. But the more prolific, high-performing groups—such as Play and Akira—generally avoid offering RaaS altogether. Their success depends on tight internal control, operational consistency, and trusted in-house operators. Approaching them for RaaS access is usually a deal breaker, as opening their brand to outside affiliates introduces noise, risk, and reputational damage. That's not to say they would never offer their services under highly unique or exceptional circumstances—but when it happens, it's rare enough to be the exception rather than the rule.
How Ransomware Affiliates Typically Emerge
What most people do not realize is that Ransomware groups start from one single person. This person can be someone who has developed source code for an encrypter and wishes to use it for profit by infecting, extorting and ransoming a company for money. Others will either have access to existing source code because it was stolen or sold to them. This can be a solo operation, or they can utilize it as a "Ransomware-as-a-Service" or "Raas". Ransomware-as-a-Service (RaaS) is a cybercrime business model, analogous to the legitimate Software-as-a-Service (SaaS) model, where skilled ransomware developers lease or sell their malicious tools and infrastructure to other criminals (known as "affiliates") for a fee or a share of the profits.
Recruitment Pathways
Productivity in the ransomware world is driven by the same necessity as the public sector: the need for skilled labor. Consequently, dark web forums and Telegram channels are used for 'Help Wanted' style advertisements to recruit affiliates. These recruitment threads are critical data points for researchers, as they represent the formal start of the affiliate lifecycle.
Research across public reporting and historical ecosystem patterns shows that affiliate recruitment generally emerges through:
- Access broker marketplaces.
- Profit-sharing partnerships advertised on forums.
- Technical skill-based filtering (vetting tasks, code tests, proof-of-ability challenges).
- Recommendations from existing members ("vouching").
- Reputation-based onboarding using pseudonymous histories.
Example below: A Profit-sharing partnership conversation between an operator and potential affiliate with vetting tasks.
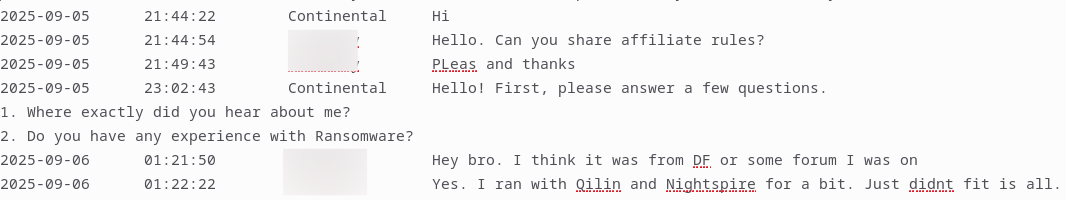
Ransomware operator discussion example.
Affiliates skill tiers:
- Tier 1 – Skilled intrusion operators; can escalate privileges, maintain persistence, and operate stealthily.
- Tier 2 – Moderately skilled; rely on purchased access, commodity tools, and playbooks.
- Tier 3 – Opportunistic actors; rely on prebuilt kits and have inconsistent tradecraft.
Tier 1: Skilled Intrusion Operators (The Elite)
This is the smallest and most dangerous group. They often operate with the stealth and precision of advanced persistent threats (APTs), making them exceptionally difficult to detect and evict.
- Primary Value: High-value, persistent access to strategic targets (e.g., large corporations, critical infrastructure). They establish deep footholds that can be maintained for long periods.
- Skill Profile: Expert-level in multiple domains (reverse engineering, networking, advanced exploitation). They can write their own custom tools (zero-day exploits are sometimes attributed here).
- Tradecraft: Stealthy and evasive.
- Escalation and Persistence: They don't rely on known vulnerabilities/tools; they can identify and exploit logical flaws or misconfigurations to achieve privilege escalation and establish custom, multi-layered persistence mechanisms.
- Lateral Movement: Utilize fileless or living-off-the-land (LOTL) techniques (PowerShell, WMI, scheduled tasks) to move through the network silently, blending in with legitimate traffic.
- Access Method: Primarily through sophisticated, targeted phishing/spear-phishing campaigns or by exploiting zero-day or recently patched, high-impact vulnerabilities.
- Goal: To maintain long-term, undetectable access to sell to high-paying buyers (like top-tier Ransomware-as-a-Service groups) or to execute operations themselves.
Tier 2: Moderately Skilled Operators (The Bulk)
These operators form the essential bridge between the entry-level actors and the sophisticated threat groups. They are crucial for scaling operations and increasing the overall volume of successful intrusions.
- Primary Value: Volume and reliability. They quickly turn purchased/easy access into a more stable, monetizable foothold.
- Skill Profile: Intermediate-level. They are proficient in executing well-defined playbooks and know how to use industry-standard hacking tools effectively.
- Tradecraft: Standardized and efficient.
- Escalation and Persistence: They use commodity tools readily available on underground forums (e.g., Mimikatz, BloodHound, commercial/cracked penetration testing suites). They focus on exploiting known misconfigurations or vulnerabilities (N-day exploits).
- Access Method: They often purchase initial access (stolen RDP credentials, VPN credentials, web shell access) from Tier 3 actors or specialized Initial Access Brokers (IABs). They then use their skills to "harden" this access, making it more resilient for the final buyer.
- Reliance: Heavily rely on playbooks (documented procedures) provided by the groups they affiliate with to ensure a consistent, repeatable outcome.
- Goal: To establish a reliable access point (e.g., a reverse shell, persistent VPN access, or domain administrator credentials) that can be quickly sold for a premium.
Tier 3: Opportunistic Actors (The Entry Point)
This is the largest tier, representing the entry level of the cybercrime ecosystem. They are often low-budget, high-volume actors who focus on casting a wide net.
- Primary Value: Raw, low-quality access. They provide the sheer volume of targets that other tiers or criminal groups can filter and exploit.
- Skill Profile: Low-to-beginner level. Their knowledge is often limited to the operation of pre-built tools and kits.
- Tradecraft: Inconsistent and noisy.
- Reliance: Almost exclusively rely on prebuilt kits and commodity malware (e.g., off-the-shelf info-stealers, cheap Remote Access Trojans - RATs). They may lack the ability to effectively customize or troubleshoot their tools.
- Access Method: Primarily through spray-and-pray techniques like massive phishing campaigns, scanning the internet for systems with default or weak credentials, or exploiting common, years-old vulnerabilities.
- Inconsistency: Their methods often generate a high volume of noise, making their intrusions easier to detect, leading to an inconsistent tradecraft and a high failure rate.
- Goal: To quickly gain a basic foothold (like a compromised user account or a single infected endpoint) and then quickly sell that raw access on the dark web for a low price, often to Tier 2 operators.
Ransomware Group Dynamics & Affiliate Ecosystem Structures
Ransomware programs vary widely in structure, gatekeeping, and operational focus. Understanding these differences is critical for safe, passive HUMINT research.
The structure focus is: Closed, Semi-Open, and Referral-Only Ecosystems pertaining to RaaS.
- Closed Programs: Invite-only, no response to outsiders, rely on internal trust networks. Only perimeter signals can be observed.
- Paid-Access / Fee-Based Programs: Require a fee or revenue share; interaction is transactional and limited.
- Referral-Driven Programs: Require a vouch from an existing affiliate; highly cohesive and coordinated.
Ransomware Program Structure
| Topic | Gatekeeping / Access Model | Operational Focus & Research Notes | Examples of Groups |
|---|---|---|---|
| Closed Programs | Invite-only, no response to outsiders, rely on internal trust networks. | Secrecy of deals is paramount. Only perimeter signals can be observed. Members often come from previously successful, closed operations. | Play, Black Basta, Royal |
| Paid-Access / Fee-Based Programs | Often use a "Ransomware-as-a-Service" (RaaS) model where affiliates pay a fee or revenue share to use the malware and infrastructure. | Interaction is transactional and limited. Core developers focus on code, while affiliates handle the attacks. Offers a lower barrier to entry for affiliates. | LockBit, REvil (Sodinokibi), DarkSide, Hive, BlackCat (ALPHV), Conti |
| Referral-Driven Programs | Require a vouch from an existing, trusted affiliate; fosters highly cohesive and coordinated operations. | Access is based on social proof and reputation within the criminal underworld. This tight-knit structure promotes trust and consistency in operations. | Conti, LockBit, DarkSide, REvil |
Different Operational Models
1. Hybrid Ransomware + Extortion (IAB, 80/20 Split 90/10 Split)
- Uses Initial Access Brokers to acquire footholds
- Affiliates perform intrusion, encryption, negotiation
- Fast, predictable operations
Qilin Ransomware affiliate 80/20 spit structure
2. Extortion-Only Models
- No encryption; fast monetization
- Low tooling requirements
- Short operational timelines
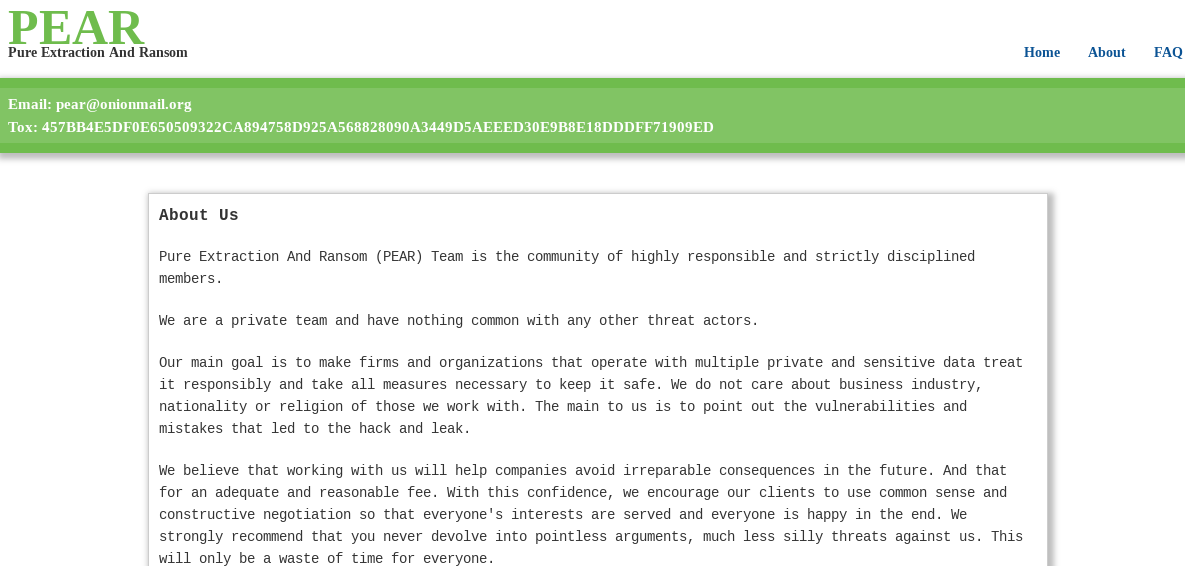
PEAR Ransomware group Extortion Team
3. Full-Stack Internal Crews
- Conduct all operations internally
- Strong internal coordination, unified tooling
- Methodical, longer-duration intrusions
PLAY Ransomware group Team
| Ransomware Program Structure | Gatekeeping / Access Model | Operational Focus & Research Notes | Examples of Groups & Models |
|---|---|---|---|
| Hybrid Ransomware + Extortion (IAB Model) | Varies widely (RaaS, Referral). Relies heavily on external Initial Access Brokers (IABs) for footholds. | Affiliates perform intrusion, encryption, and negotiation. Operations are fast and predictable. Profit splits are common (e.g., 80/20, 90/10 favoring the affiliate). | LockBit (heavy IAB usage), BlackCat, Conti |
| Extortion-Only Models | Often RaaS or low-barrier entry. | Focuses solely on data theft and public release/sale, with no encryption required. Requires low tooling, allowing for fast monetization and short operational timelines. | Lapsus$ (extortion only crew), Avaddon (sometimes used this approach) |
| Full-Stack Internal Crews | Closed, invite-only, highly trusted internal teams. | Conduct all operations internally, from initial access to negotiation. Strong internal coordination and unified tooling result in methodical, longer-duration intrusions. | Play, Black Basta, Royal |
Understanding these models helps researchers predict behavior before attempting to collect intelligence from ransomware groups. Intelligence gathering without an understanding of the adversary's model is a shot in the dark. By applying the "Know Thy Enemy" principle, an analyst transforms raw data into predictive foresight. Understanding, not only protects the analyst by helping them avoid "psychological traps" set by the adversary but also provides law enforcement with the precise leverage points needed to dismantle a group's entire infrastructure before it can scale.
Effective Listening and Tactical Empathy
In the context of the SHADOW framework for tracking ransomware affiliates, Effective Listening is considered an active and essential skill for gathering high-quality intelligence. Its importance stems from the psychological principle that most valuable insights are revealed naturally when a target feels heard and safe to explain their situation freely.
Key Elements:
- Mirroring statements – encourages more talking without pressure.
- Minimal encouragers ("Go on…", "Interesting…") – supports natural disclosure.
- Strategic silence – people often fill silence with more information.
- Labeling emotions ("Sounds like that frustrated you…") – reduces defenses and increases honesty.
Insight comes most often not from answers, but from what is said after the answer.
Example below: The engagement begins with a standard greeting and a request for an introduction from the ransomware group. Following this initial exchange, the operators steer the dialogue toward more technical or operational requirements, requesting specific information necessary to advance the discussion.
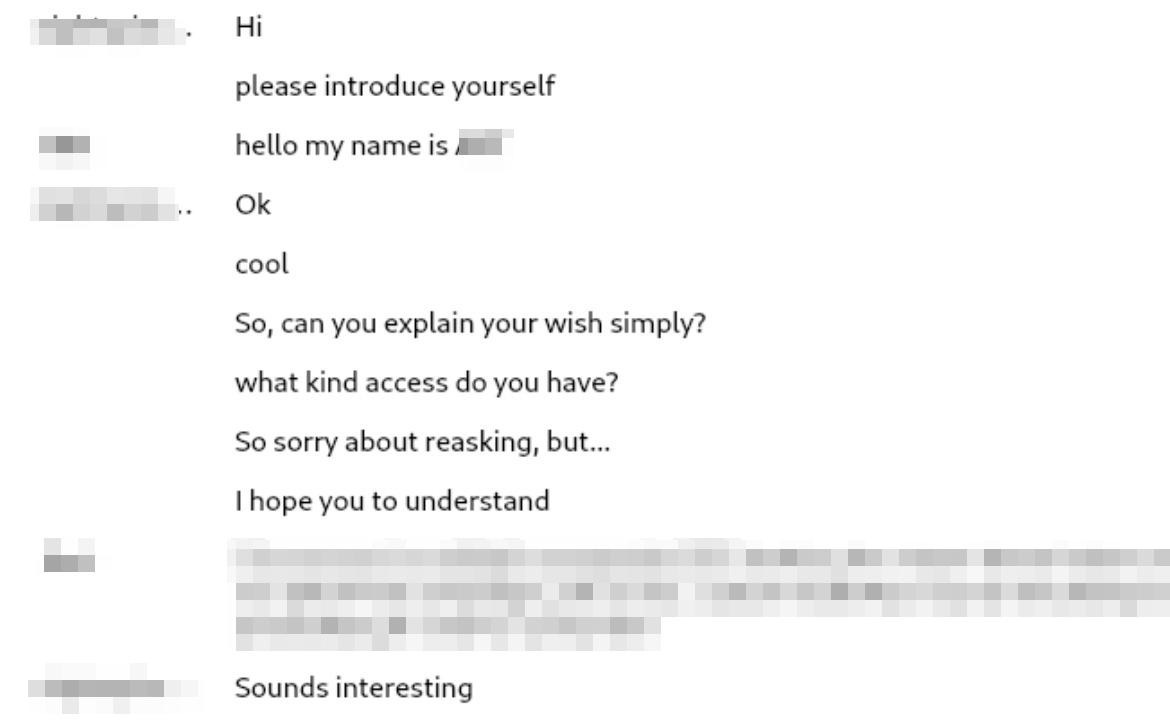
Affective listening example with ransomware operator.
Example below: Each ransomware group maintains unique onboarding procedures and affiliate rules. For the analyst, effective listening is critical; it allows for the decryption of an operator's speaking patterns and reveals when individual communications are intended as broader directives for their entire affiliate network. It's not one operator the analyst is addressing, it's the entire ransomware group.
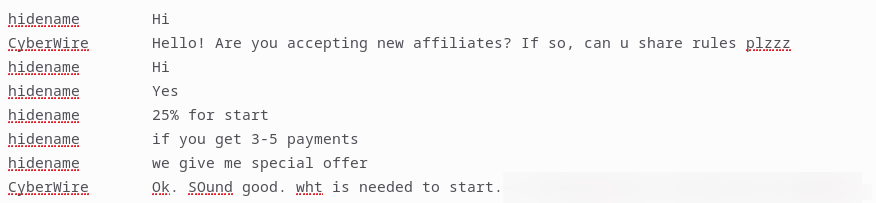
Example below:
Ransomware groups differ in their level of disclosure. When a group provides a detailed list of requirements, it presents a critical window for the analyst to capture high-fidelity notes on their recruitment and technical workflows.

Tactical Empathy is not sympathy or agreement — it is understanding how the other person sees the world and reflecting it back to them. It is the greatest tool you will have in your arsenal for gathering ransomware intelligence. Historically, cyber analysis has been framed through a binary 'us versus them' lens. However, effective HUMINT requires a shift in perspective: recognizing that threat actors are subject to the same psychological drivers and stressors as anyone else. By humanizing the adversary, analysts can more accurately predict their behaviors and identify operational vulnerabilities.
Tactical Empathy Examples: "It feels like, It looks like, It seems like and How can I do that?".
"It feels like you're under pressure to move quickly, so stability matters less to you than speed."
"It seems like you run a very tight crew and care about details".
"It looks like this matters to you most and should be considered sacred to the group."
What this does:
- Shows you understand their perspective.
- Makes them feel safe expressing details.
- Build connections without endorsing actions.
Empathy is influence — not approval.
Where These Skills Become Valuable. Information tends to surface when a person feels:
- Heard
- Understood
- Not judged
- Viewed as human
- Safe to explain freely
When this happens, people naturally reveal information such as:
- Motivations and frustrations.
- Processes and decision logic.
- How systems or operations work.
- Weaknesses or internal conflicts.
This requires no deception, no illegal access, no boundary crossing — just psychology. Active Listening + Tactical Empathy opens doors that force never could.
In the example below: An operator has established trust but wants to feel more secure about the discussion and feel more involved in decisions. When asked 'How can I do that?" The operator can address what makes them feel safer.
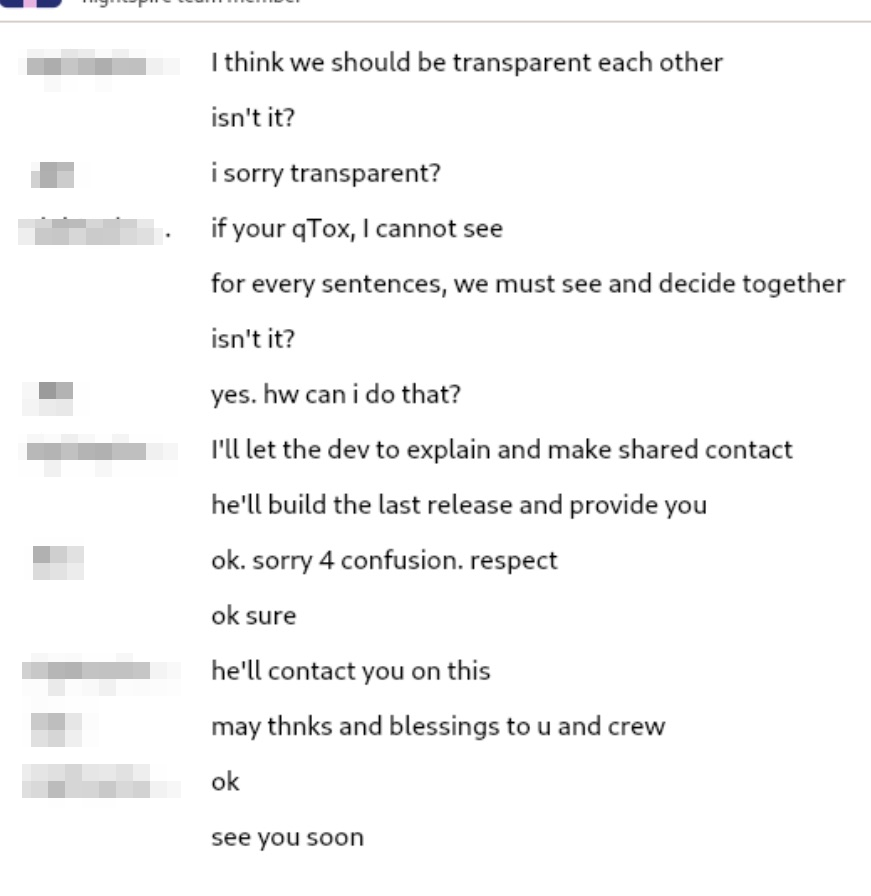
TOX Operator conversation
Example A: Once an operator has established basic trust, they will often seek further details to vet the potential affiliate. They may ask questions such as: 'Tell me about yourself,' 'Who do you cooperate with?' and 'How long have you been on this topic?' These are excellent opportunities for the analyst to build rapport. By applying Tactical Empathy, the analyst can pivot the conversation with a question like, 'How do I start with you guys?' which moves the focus back to the operator's process while maintaining the persona.
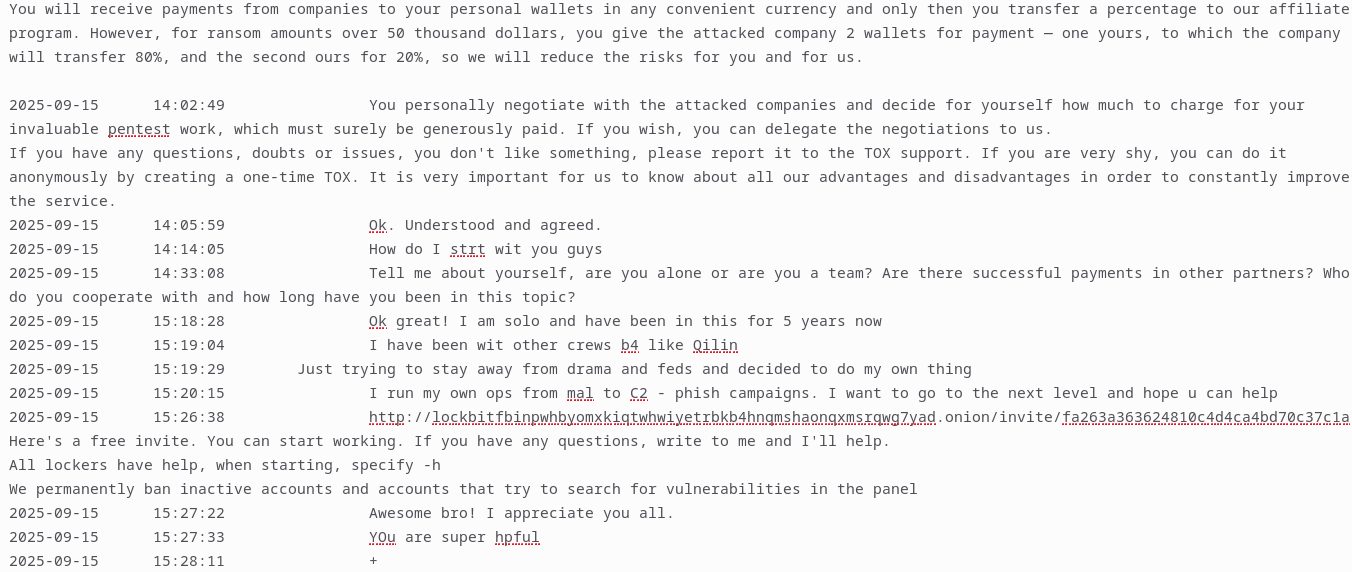
TOX Operator conversation
Example B: Once trust is established, the operator may inform the potential affiliate that updates are required and express a willingness to work through any necessary improvements. The operator might even directly challenge the affiliate's identity—asking if they are involved in 'AV research'—and share personal stories, such as receiving communications from the FBI. These moments are critical, as the operator is using personal anecdotes to test the affiliate's reaction and solidify the bond through shared adversity.
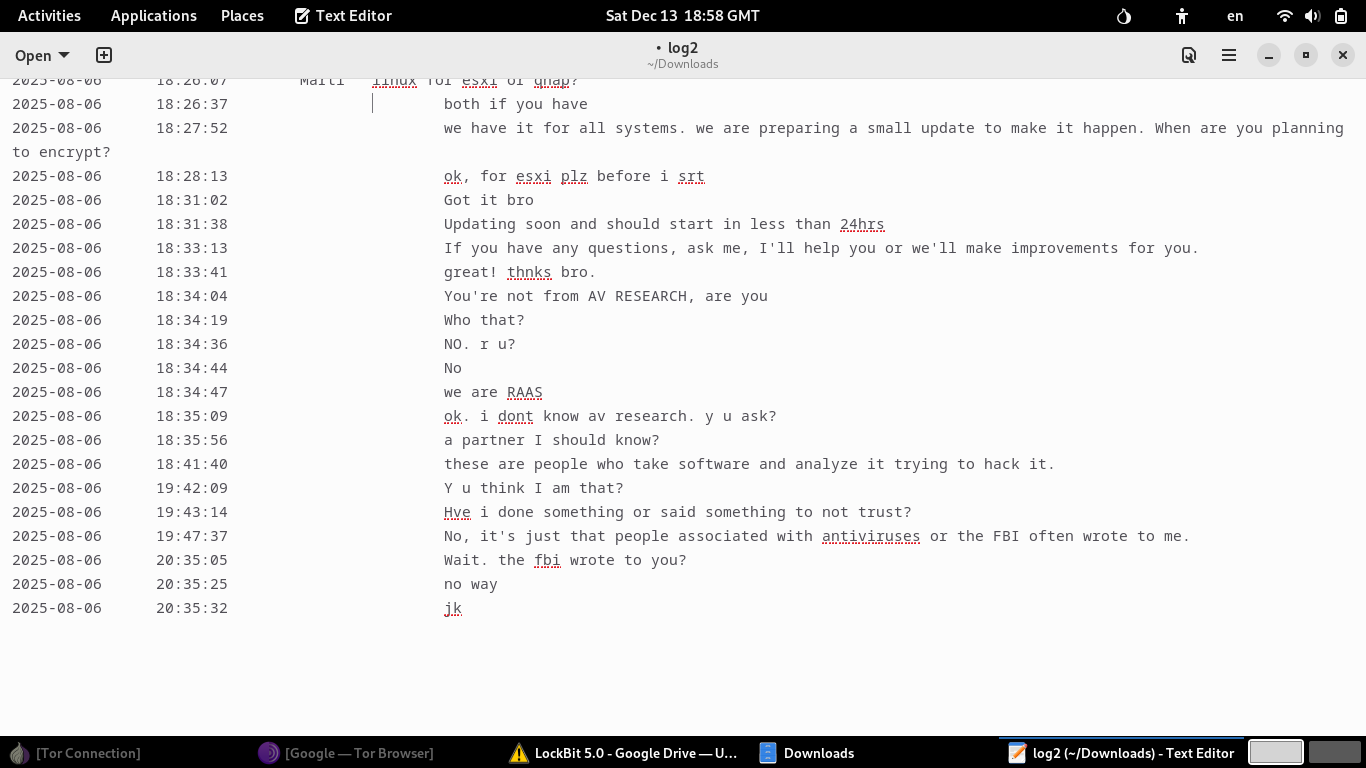
TOX Operator conversation
Example C: One tactic an analyst can use within the Tactical Empathy framework is an Accusation Audit. In the example below, the analyst proactively addresses a potential deal-breaker by stating they have no money but still wish to join the group. Even after hearing this, the operator chose to continue the conversation, demonstrating how addressing negative assumptions upfront can actually strengthen the dialogue and keep the engagement moving forward.
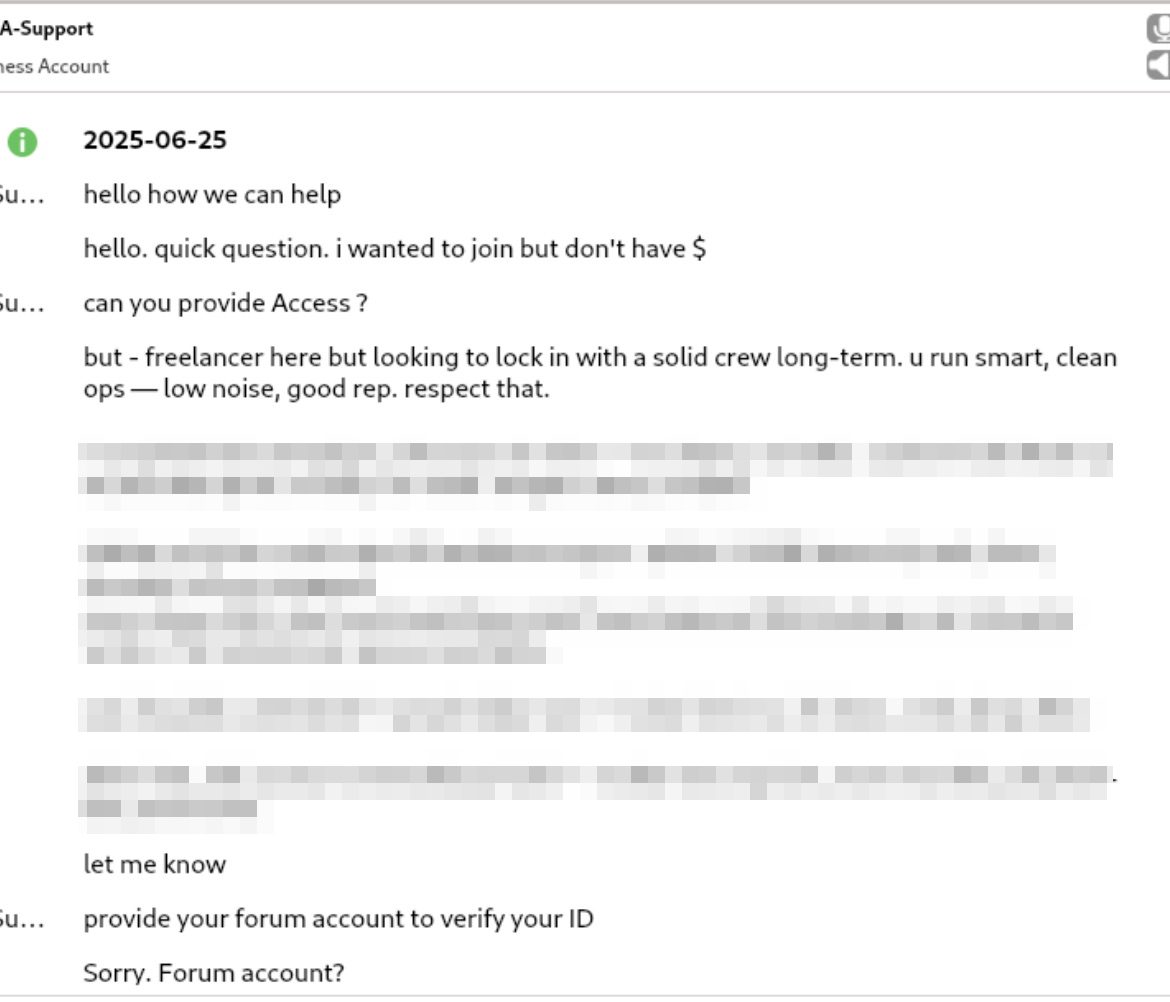
TOX conversation about vetting
Example F: "In one instance, a LockBit 5.0 operator engaged in a standard conversation regarding vetting procedures and affiliate rules. By maintaining the dialogue and asking 'how' questions—a core component of Effective Listening and Tactical Empathy—the analyst was able to build significant rapport. This strategic approach eventually led the operator to grant the analyst panel access to the ransomware infrastructure, demonstrating how behavioral techniques can bypass traditional technical barriers.
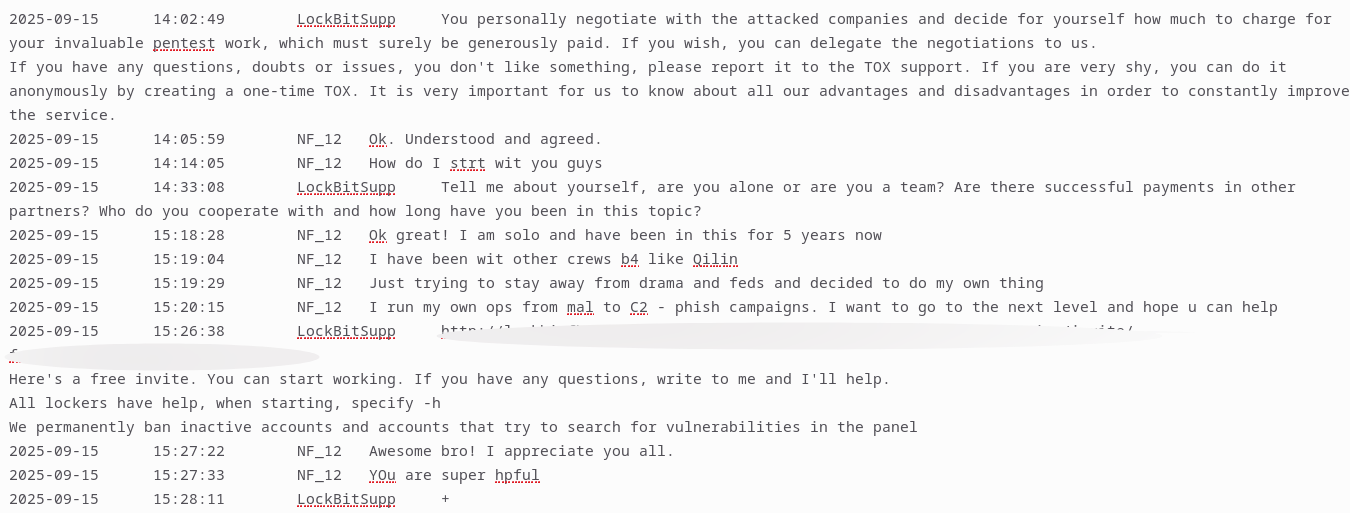
TOX LockBit5.0 vetting and Infrastructure details.
LockBit5.0 Ransomware Panel Overview
Ethical Analysis of Affiliate Behavior
Understanding the behavior of ransomware affiliates requires examining the ethical landscape they operate within, not just the technical mechanics of their intrusions. A HUMINT-driven view reveals that affiliates often navigate a shifting moral terrain shaped by self-justification, group norms, personal boundaries, and the structural incentives of the ransomware economy. (The below examples were obtained through a synthetic account while researching ransomware groups.)
1. Self-Justification and Moral Licensing
Affiliates frequently rationalize their actions by reframing them as retaliation against institutions, "victimless" cybercrime, or simply a way to survive financially. This self-justification allows them to minimize or disregard the significant human harm caused by their actions, including operational disruptions, economic loss, and community-level consequences.

Scattered Lapsus$$ Hunters Telegram Channel
2. Ethical Displacement
Within many crews, affiliates distribute tasks across multiple individuals—initial access brokers, infrastructure operators, deployers, and negotiators. This compartmentalization allows each participant to claim, "I only did my part," shifting responsibility away from themselves and diffusing moral accountability across the group.
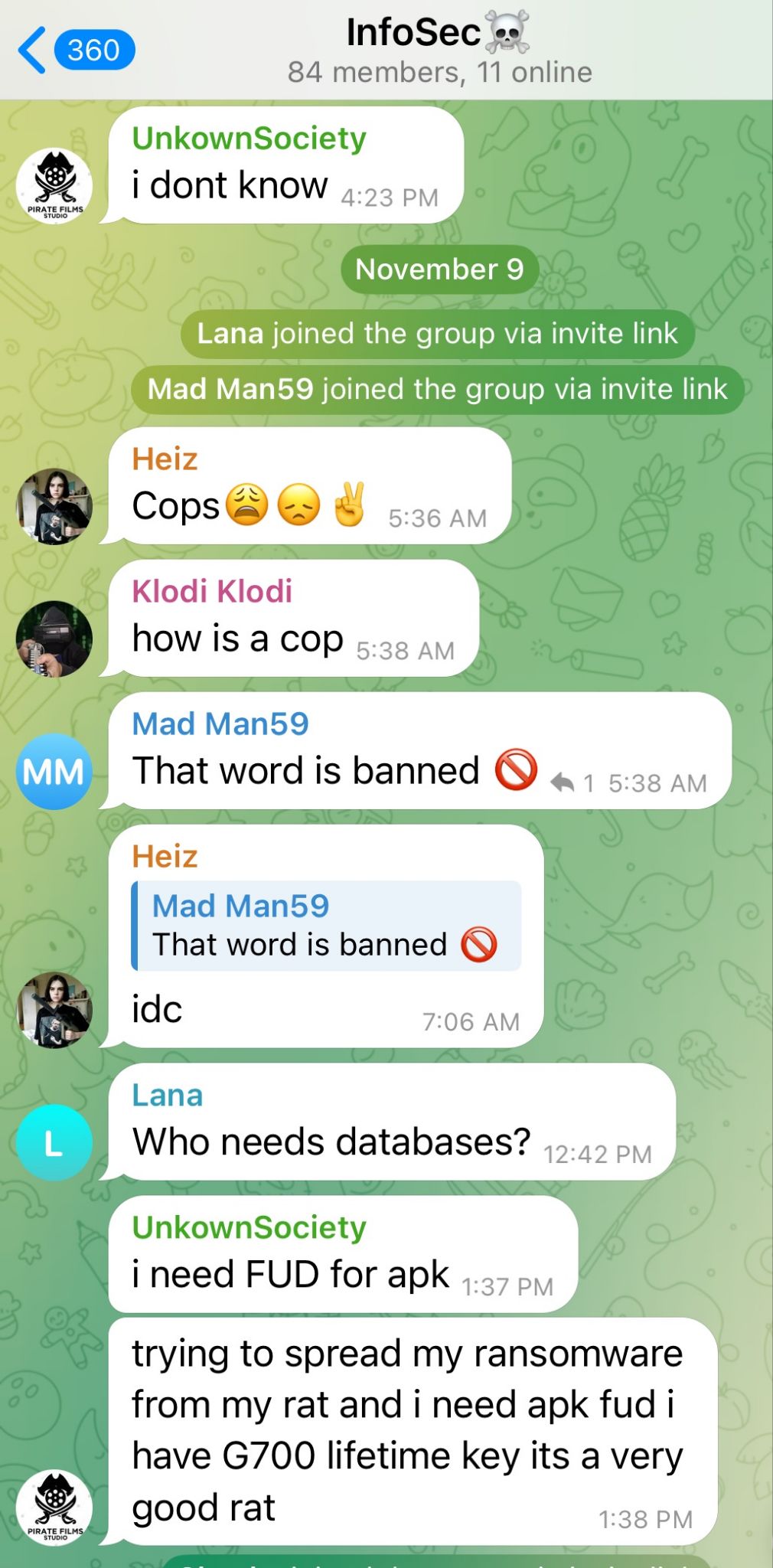
New Ransomware Telegram Channel
3. Normalization Inside the Subculture
Inside ransomware ecosystems, harm becomes normalized. Actions that would be ethically unacceptable in mainstream society are reframed within the subculture as routine, expected, or even signs of competence. Group chats, leak sites, and underground forums reinforce this normalization, shaping a sense of belonging that overrides ethical objections.

Scattered Lapsus$$ Hunters Telegram Channel
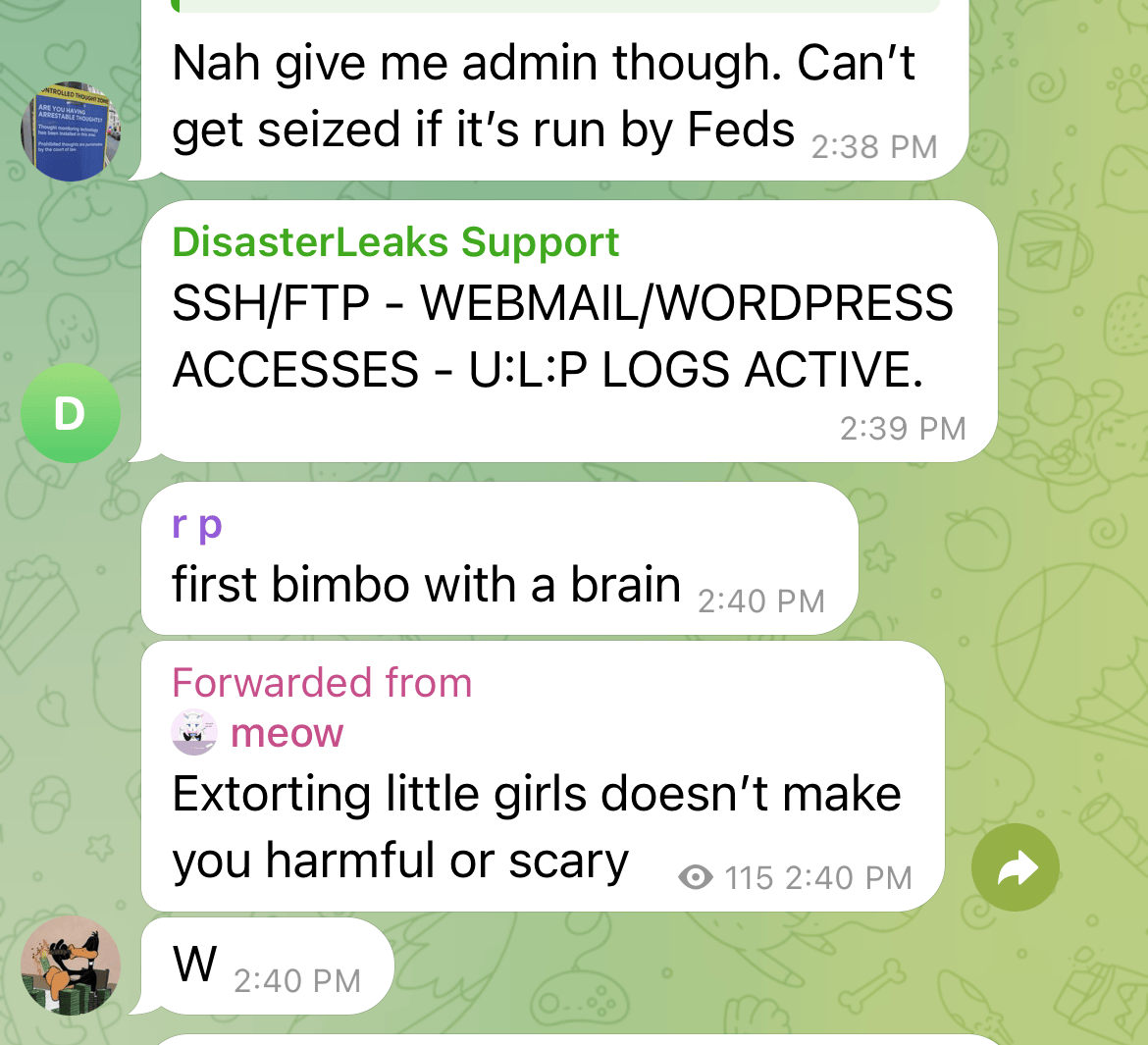
Scattered Lapsus$$ Hunters Telegram Channel
4. Incentives Drive Ethical Decay
The affiliate payout model rewards maximum disruption. The more damage inflicted—or the more leverage created—the higher the potential profit. This incentive structure naturally encourages escalation, indifference to victim type, and the erosion of any pre-existing moral boundaries.
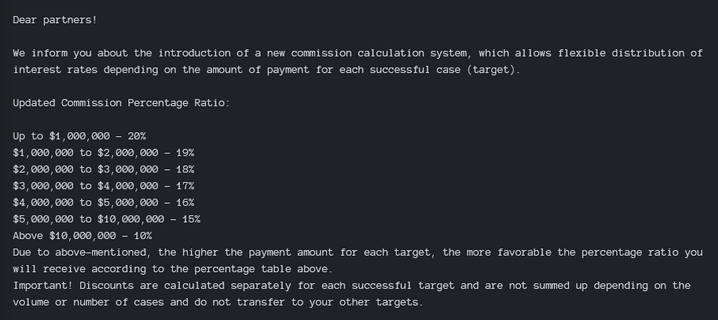
Qilin group incentives
Distance From Consequences
Most affiliates never see the human impact of their work. The suffering is abstract: disrupted surgeries, delayed treatments, family stress, and community instability. This distance creates ethical blindness—an inability or unwillingness to connect technical actions with real-world outcomes.
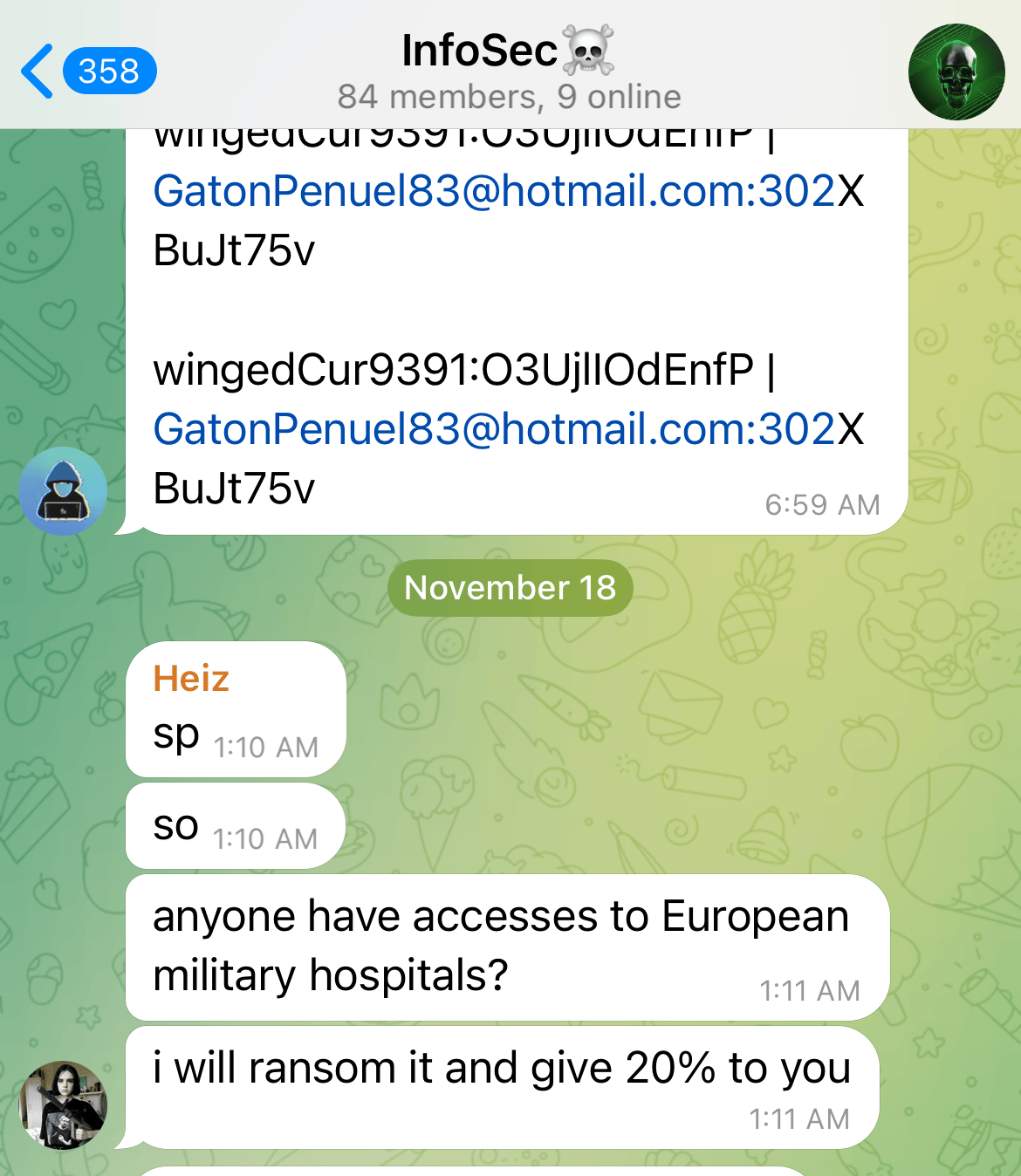
New ransomware group Telegram Channel
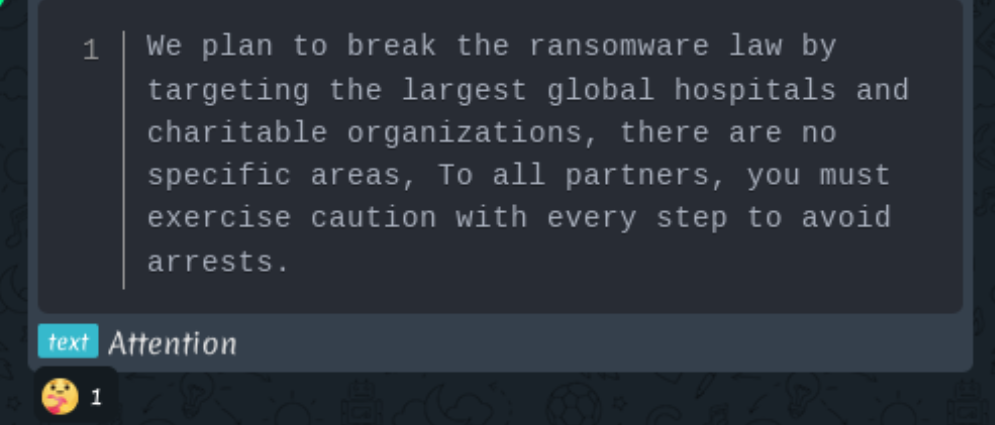
Nova Ransomware group chat announcement
SHADOW - A HUMINT Driven Workflow
Once you've understood the principles of SHADOW and utilized proper OPSEC measures described above into practice, you'll need to select an OSINT approach for gathering ransomware intelligence. OSINT, or open-source intelligence, involves collecting and analyzing information that's publicly accessible to evaluate threats, inform decisions, or address specific questions. It's widely used by organizations as part of their cybersecurity strategy to assess security risks and uncover vulnerabilities within their IT infrastructure. Ransomware.live, Ransomware.look, and DarkwebInformer are excellent OSINT resources that provide current activity and information on ransomware activity and groups.
For example, some ransomware actors use social media to advertise and brag about data breaches. One place is on "X" formerly known as Twitter. It may seem contradicting to use a widely known platform to boast about ruining a business, but ransomware groups love the publicity. It's a great way for an analyst to keep up to date with the latest on a ransomware group.
An analyst may be fortunate enough to find a discussion about a Dark Web forum that ransomware affiliates use. This is an advantage to the analyst because they will be able to join the dark web forum with a synthetic account and utilize SHADOW to dive deeper into the ransomware ecosystem.

X Account referencing a dark web forum
After an analyst is able to obtain an address to a dark web forum, they will be able to review multiple threads and research and gather intelligence of ransomware groups. Obtaining access to a dark web forum address for passive intelligence collection is especially valuable for ransomware research, as it allows analysts to observe the ecosystem that enables ransomware operations without direct interaction or attribution risk. From a defensive standpoint, these forums provide early insight into ransomware group dynamics, affiliate recruitment, access-broker activity, pricing for network access, and discussions around payload deployment, encryption performance, and negotiation tactics. Analysts can track how ransomware groups evolve their tradecraft, respond to law enforcement pressure, abandon or rebrand operations, and exploit gaps in organizational defenses.
This visibility helps defenders anticipate ransomware campaigns before they materialize, understand which initial access vectors are being favored, identify emerging extortion techniques, and translate adversary chatter into proactive controls, improved detections, and more informed incident response planning.
rehubcom.pro darkweb forum
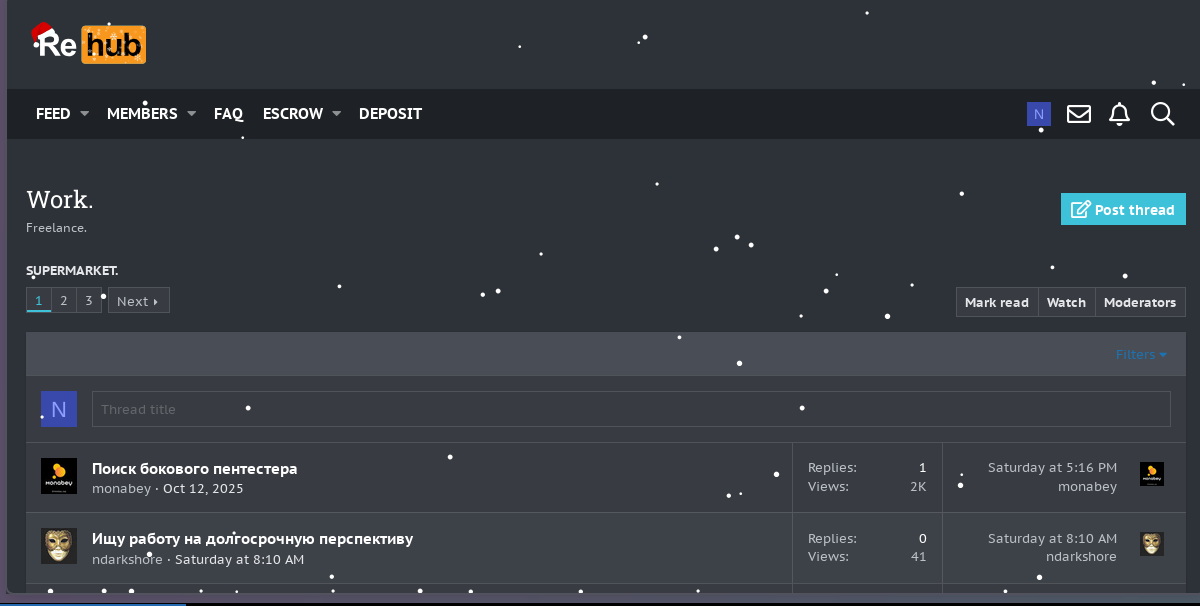
In the pictures below, an analyst is able to view multiple threads that pertain to ransomware groups and ransomware as a service (RaaS) groups and what is required for their services.Understanding a ransomware group's stated rules, operational boundaries, and what they provide to affiliates is highly beneficial for analysts conducting passive intelligence collection, as it strengthens OPSEC while improving analytical accuracy. By observing how groups define prohibited targets, negotiation behavior, data handling practices, and support expectations—without engaging—analysts can better distinguish genuine group activity from imitators or opportunistic actors, reducing the risk of misattribution.
This knowledge also helps anticipate how a group is likely to behave during an incident, what pressures may influence negotiations, and which claims are credible, all while maintaining strict non-interaction. Leveraging adversary self-published rules in this way allows defenders to extract insight without exposure, turning the group's own governance and marketing into a low-risk intelligence advantage.

The Gentlemen RaaS thread
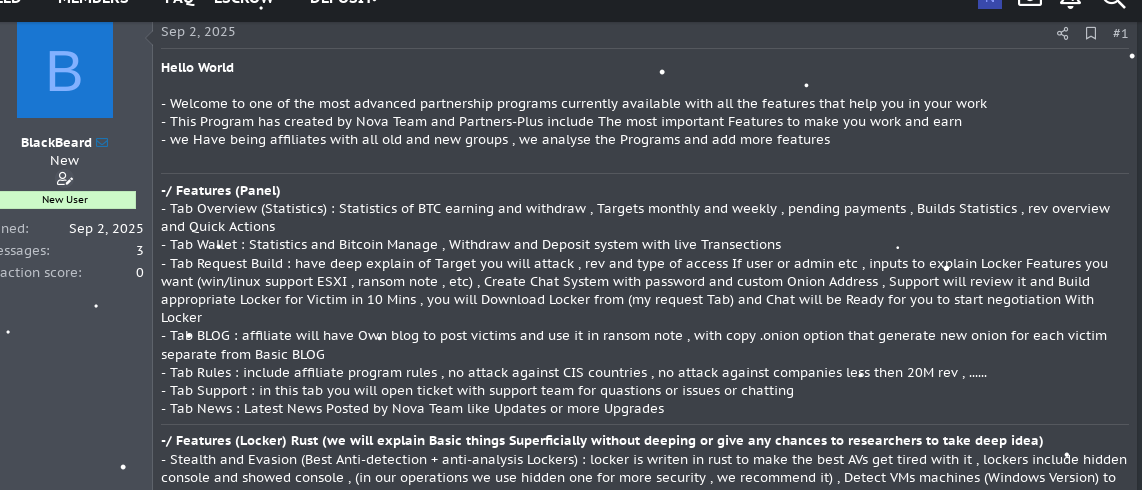
Nova RaaS thread
In addition to tracking tradecraft and access-broker activity, these forums reveal the dysfunction and rivalry between ransomware groups operating in the same environment, including disputes over affiliates, stolen data, and broken profit-sharing agreements. Analysts can also directly observe how actors evaluate and criticize each other's ransomware strains—publicly mocking weak encryption, unstable builders, poor OPSEC, unreliable decryptors, or negotiation panels that fail under pressure.
These candid assessments expose which strains are considered effective, which are avoided, and why certain families lose affiliates or credibility over time. For defenders, this insight helps explain shifts in ransomware popularity, predicts fragmentation or rebranding events, and highlights operational weaknesses that may increase attacker errors, negotiation failures, or recovery opportunities during incidents.
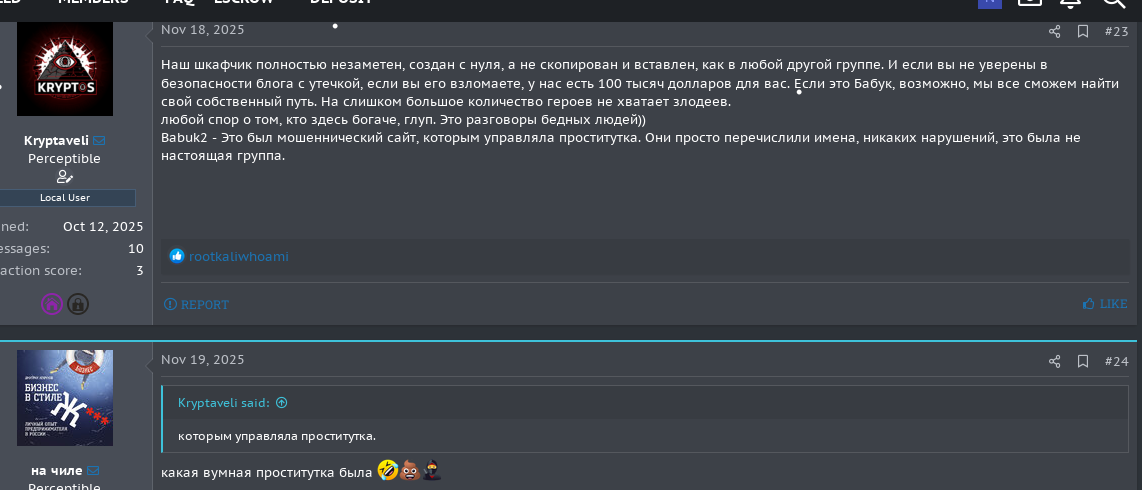
Ransomware affiliates discussing a RaaS service
Emerging Threat Actors: Exploiting the Growth Phase
Analysts can also discover newly emerging ransomware groups actively recruiting on dark web forums. For instance, the group below established a Telegram channel specifically for recruitment, inviting interested parties to contact the operator directly. These early-stage interactions provide a beneficial moment to apply the SHADOW framework; because these groups are not yet established, they are often more open to conversation and more likely to reveal operational details. (The examples below were obtained using the synthetic personas 'NF_12' and 'Toxic Rabbit' during active ransomware research).
During the initial contact process, the operator typically outlines the operational parameters of the group. This includes reviewing critical details such as:
- Ransomware features and instructions: Defining the capabilities of the malware.
- Profit-sharing percentages: Establishing the financial terms of the partnership.
- Encryptor details and deployment instructions: Providing the technical guidance for execution.
- Threat actor backstory details: Sharing context that helps build rapport and trust.
By paying close attention to these specific items, an analyst can gain a clear understanding of the group's technical sophistication and organizational maturity.
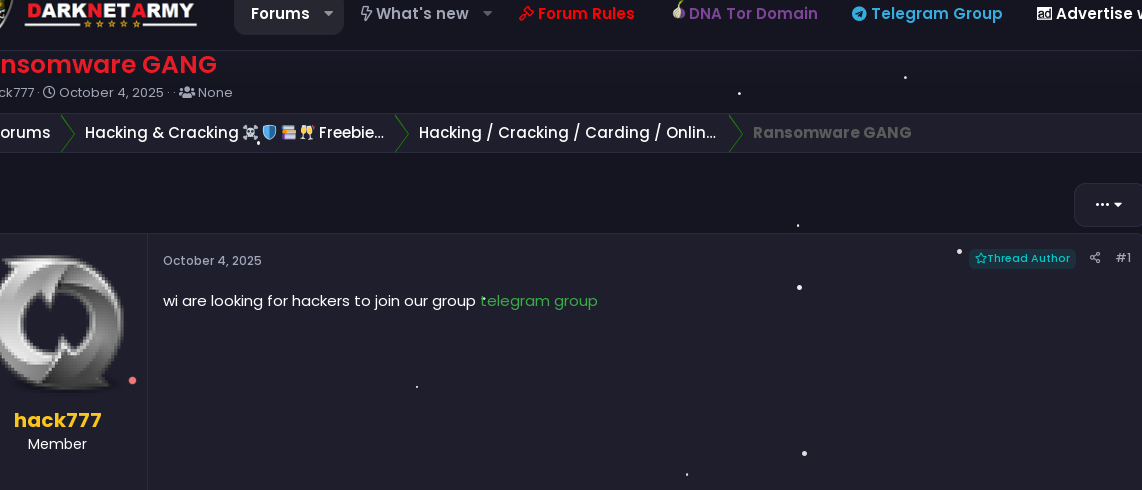
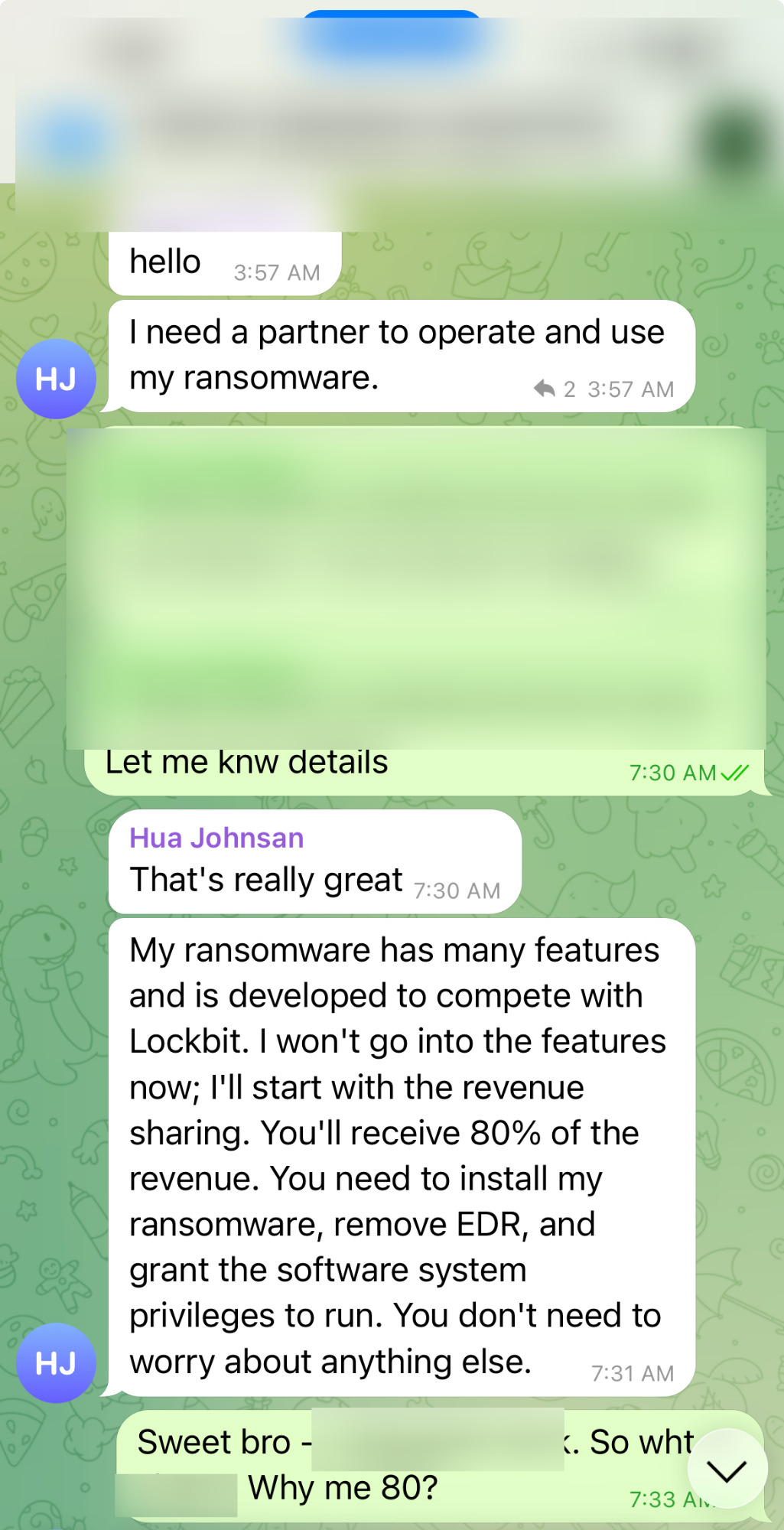
Ransomware group Telegram channel post.
Telegram conversation summary:
During the interaction, the operator specifically stated the need for someone to 'Partner and use my ransomware.' These choice of words are significant, as they symbolize both a desire for control and a foundational level of trust. Ultimately, the intelligence gathered from these dialogues—such as technical specifications or deployment methods—can be utilized for reverse engineering to assist future victims.
To maximize results during this initial stage, keep these core tactics in mind:
- Adopt a 'Customer' Mindset: Listen and inquire as if you were a prospective partner. This is where Effective Listening is paramount; every word used by the operator provides a clue into their operational rhythm.
- Validate Their Effort: Acknowledge the work they put into their tools. Operators often view themselves as professionals and appreciate being valued for their expertise. Utilizing Tactical Empathy in this way encourages them to lower their guard and share more details.
- Maintain Balanced Control: While the operator may feel they are leading the conversation, the analyst must subtly direct it. Maintain a passive, non-confrontational posture to avoid escalation. If the engagement becomes high-risk or ethically compromised, recognize the power of the word 'No.' It is always safer to disengage from a volatile conversation than to remain involved in a dangerous one.
Ransomware group Telegram channel post.
Ransomware group Telegram channel post.
Ransomware group Telegram channel post.
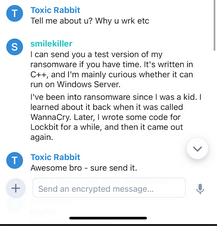
When identifying a new ransomware collective, analysts should pay close attention to the preferred communication channel. While many groups use Telegram for its ease of use, more OpSec-conscious (Operations Security) groups—like the one shown below—opt for the Tox messaging application.
By establishing a dedicated forum thread that lists their ransomware's capabilities and affiliate requirements, the group sets the stage. However, they explicitly mandate that all 'business' inquiries occur via Tox. Providing a Tox ID as the sole primary gateway serves two purposes:
- Enhanced Privacy: It utilizes a decentralized, serverless architecture that does not require a phone number.
- Selective Vetting: It moves the conversation away from the public eye of the forum into a direct, encrypted environment where the operator can conduct deeper engagement and private vetting of the analyst's persona."
- Profit-sharing structure: The group outlines the revenue split between the operators and their affiliates. In this instance it is 5-10% to the author and the remaining amount sent to the affiliate.
- Operating system requirements: This specifies which platforms the ransomware is designed to target; in our case it is all Windows devices.
- Group requirements to join: The specifics below to join are linked to having access with profitable data.
- TOX ID for communication: The owner of the thread below has a TOX ID that you can use to communicate with him.
- Encryptor build details such as encryption algorithm and more: The thread below goes over the specifics of the encryptor build, infrastructure and tools. It shows what an affiliate would achieve and how it would be appealing to new affiliates.
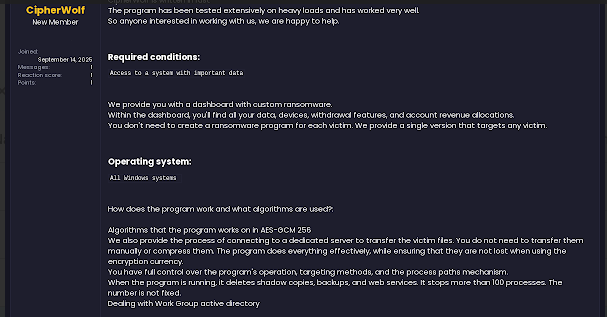
Dark web forum RaaS post
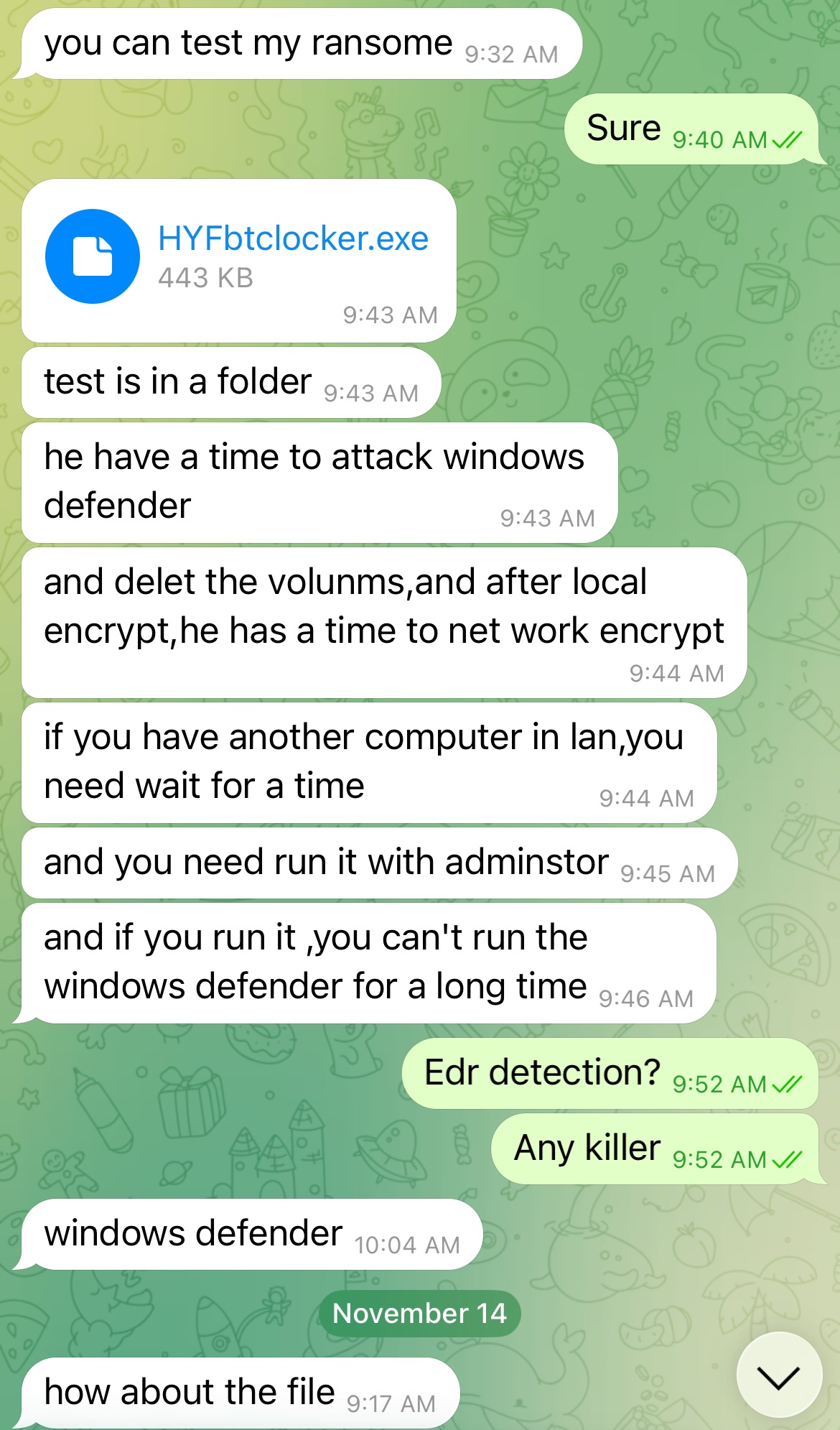
When a potential affiliate reaches out via Tox, the dialogue typically shifts toward a more in-depth exploration of the ransomware group's operational details and onboarding requirements. During this critical initial stage, keep these core tactics in mind:
- Adopt a 'Customer' Mindset: Listen and inquire as if you were a prospective client or partner. This is where Effective Listening is paramount; every word used by the operator provides insight into their organizational structure and expectations.
- Acknowledge Their Effort: Operators often take pride in their technical 'craft.' By remaining positive and asking questions about their operations, you show they are valued for their work. Utilizing Tactical Empathy in this way encourages them to speak more freely about their successes and methods.
- Maintain Balanced Control: While the operator may appear to lead the conversation, the analyst must subtly direct the engagement. It is vital to remain passive and avoid escalating into high-risk situations. If a conversation becomes volatile or ethically compromised, remember the power of the word 'No.' It is always better to terminate a problematic engagement than to remain involved in a dangerous one.
- Direct Outreach: Contact RaaS operators directly via the contact information provided in their posts or DLS "contact" sections. This method minimizes risk to your primary forum accounts.
- Introductory Hook: Lead with a high-impact opening that highlights professional capabilities, such as access to high-revenue targets in Tier-1 regions, to ensure interest.
- Objective-Driven Interaction: Maintain a "researcher" mindset—avoid over-questioning while staying focused on clear objectives, such as obtaining operational details, panel access, or malware builds.
Summary of TOX conversation:
Engaging with recruitment posts on Dark Web forums requires a calculated approach. By adopting the persona of an aspiring 'penetration tester' or affiliate, an analyst can initiate a dialogue centered on technical requirements and operational onboarding. Maintaining a polite, professional tone and projecting a sincere 'desire to belong' lowers the operator's defenses. This rapport-building often yields high-side intelligence, including access to proprietary encryptors, internal decryption tools, and even leaked training videos used to onboard new members.
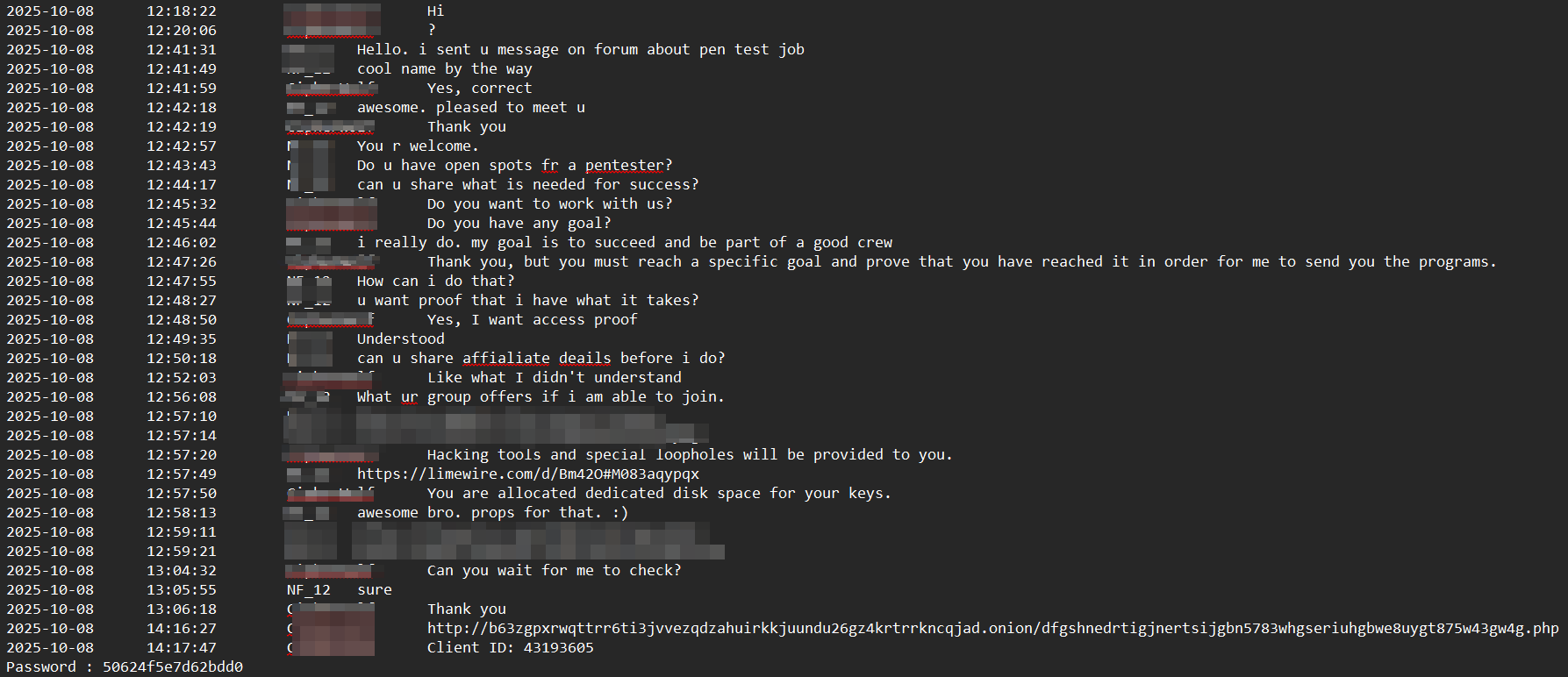
Ransomware group TOX chat
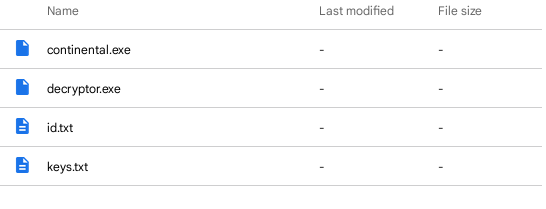
Ransomware group gathered intelligence. (Encryptor, Decryptor and keys.)
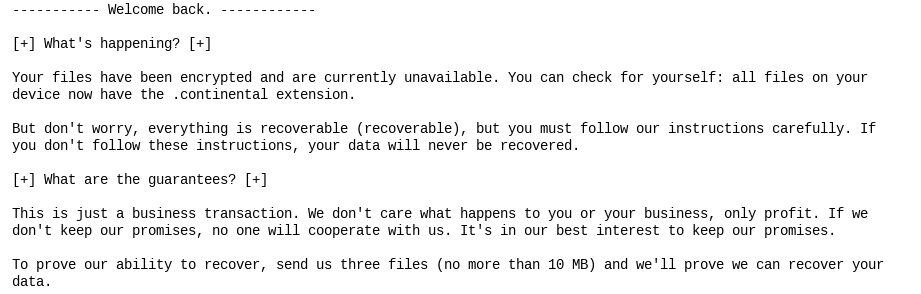
Ransomware operator's text file for victims.
Ransomware Operator video of ransomware functionality.
Communicating with emerging ransomware groups provides a unique, high-leverage window for intervention before they achieve the scale and "operational maturity" of established syndicates. In the early stages of a group's lifecycle, their infrastructure is often less resilient, and their operators are more prone to making technical and operational security errors.
When Ransomware Intelligence Becomes an Insider Threat
Ransomware research is typically aimed at understanding external threat actors, their operations, and decision-making. At times, however, deeper research can uncover unexpected dynamics, such as insider threat scenarios, within or adjacent to these groups. Because ransomware ecosystems rely heavily on trust, access, and reputation, fractures in those relationships—misuse of access, divided loyalties, or internal abuse—can become visible to researchers. When this occurs, it presents a unique opportunity: not only to better understand the ransomware group itself, but to gain real-world insight into how insider threats develop, operate, and remain concealed.
In the Example below: Operating under the synthetic persona 'Toxic Rabbit,' the analyst documented an interaction where an insider threat actor proactively reached out to a ransomware group to sell sensitive corporate data for profit. The actor provided an itemized list of accessible assets and outlined specific ways the ransomware group could facilitate a breach. Significantly, the ensuing dialogue yielded critical attribution clues, suggesting that at least one member of this emerging group originated from the
LockBit ecosystem. Insider threat Telegram channel discussion
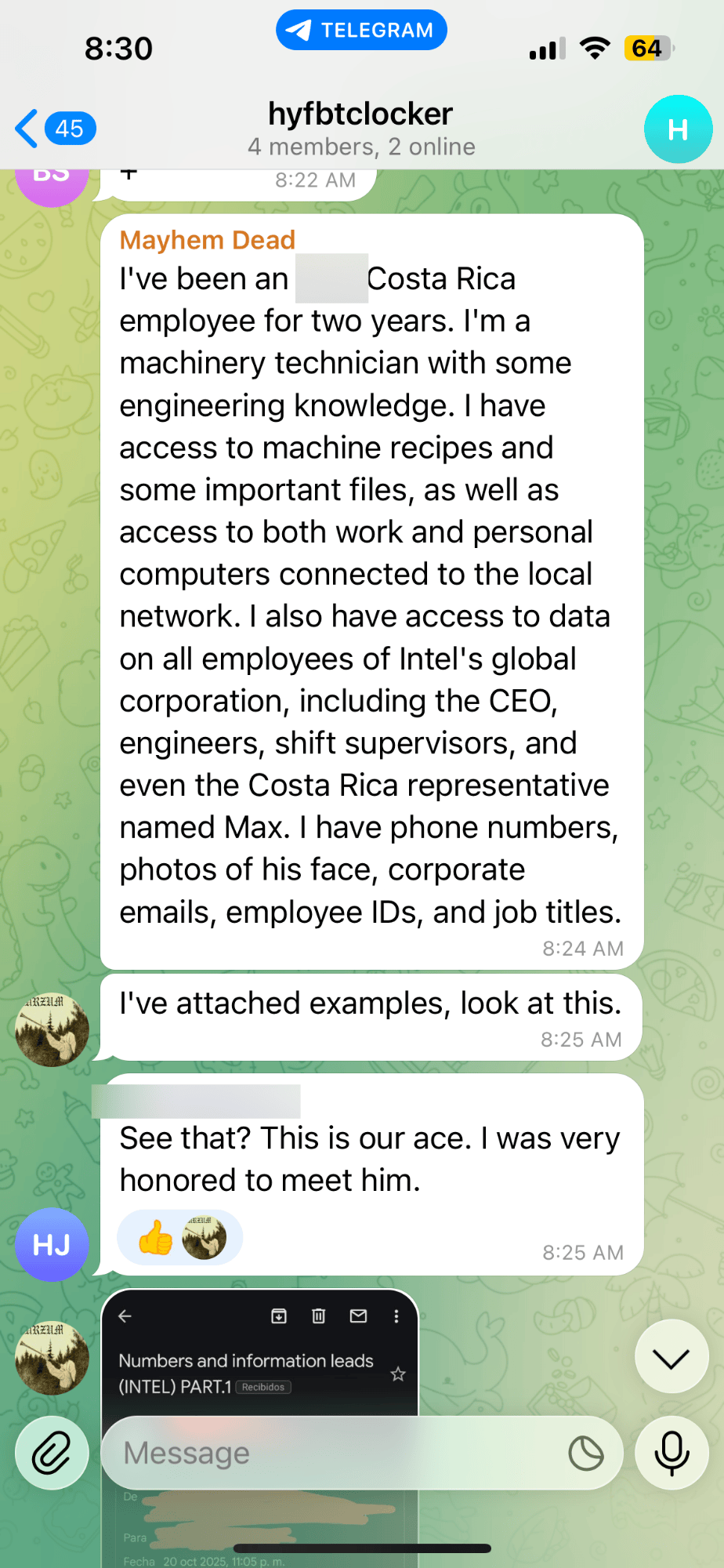
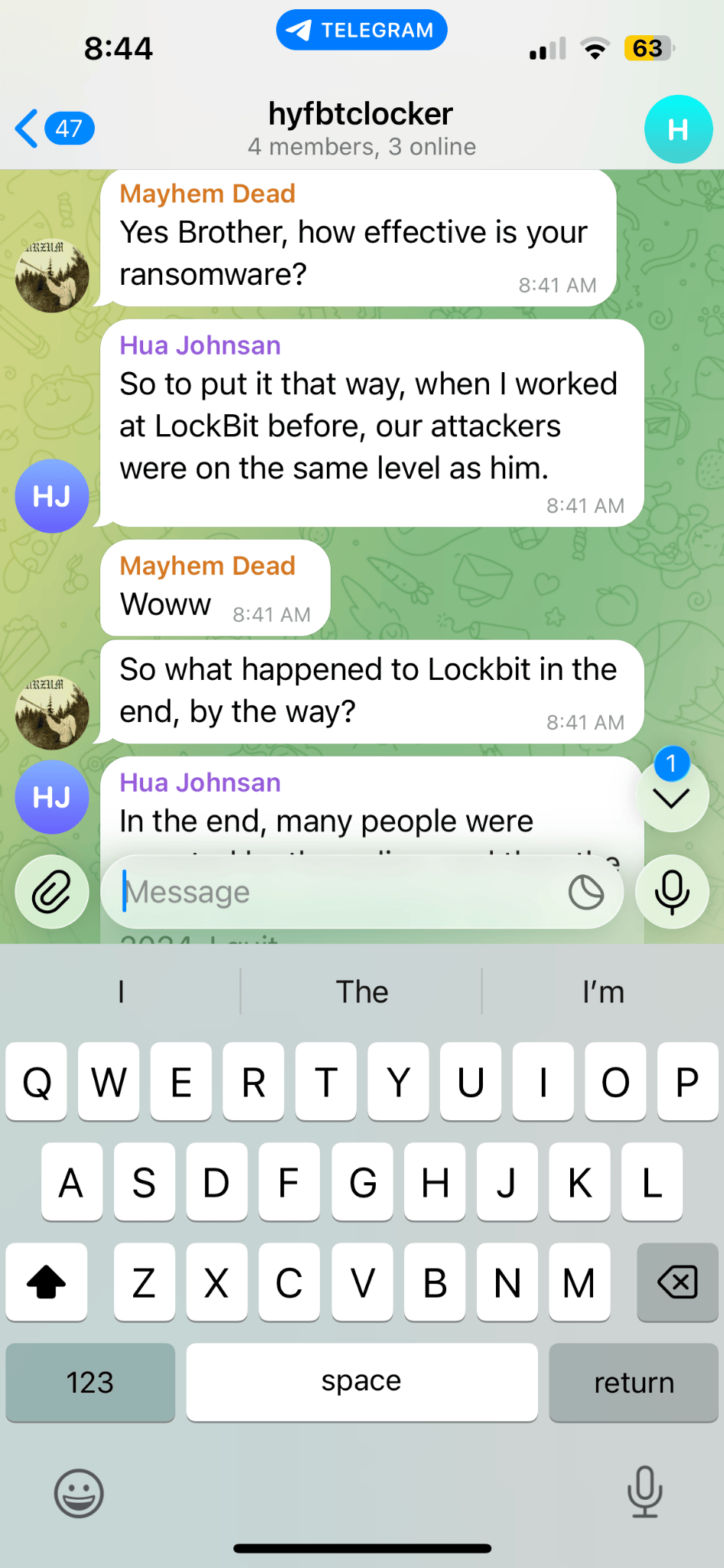
New Ransomware Telegram channel discussion
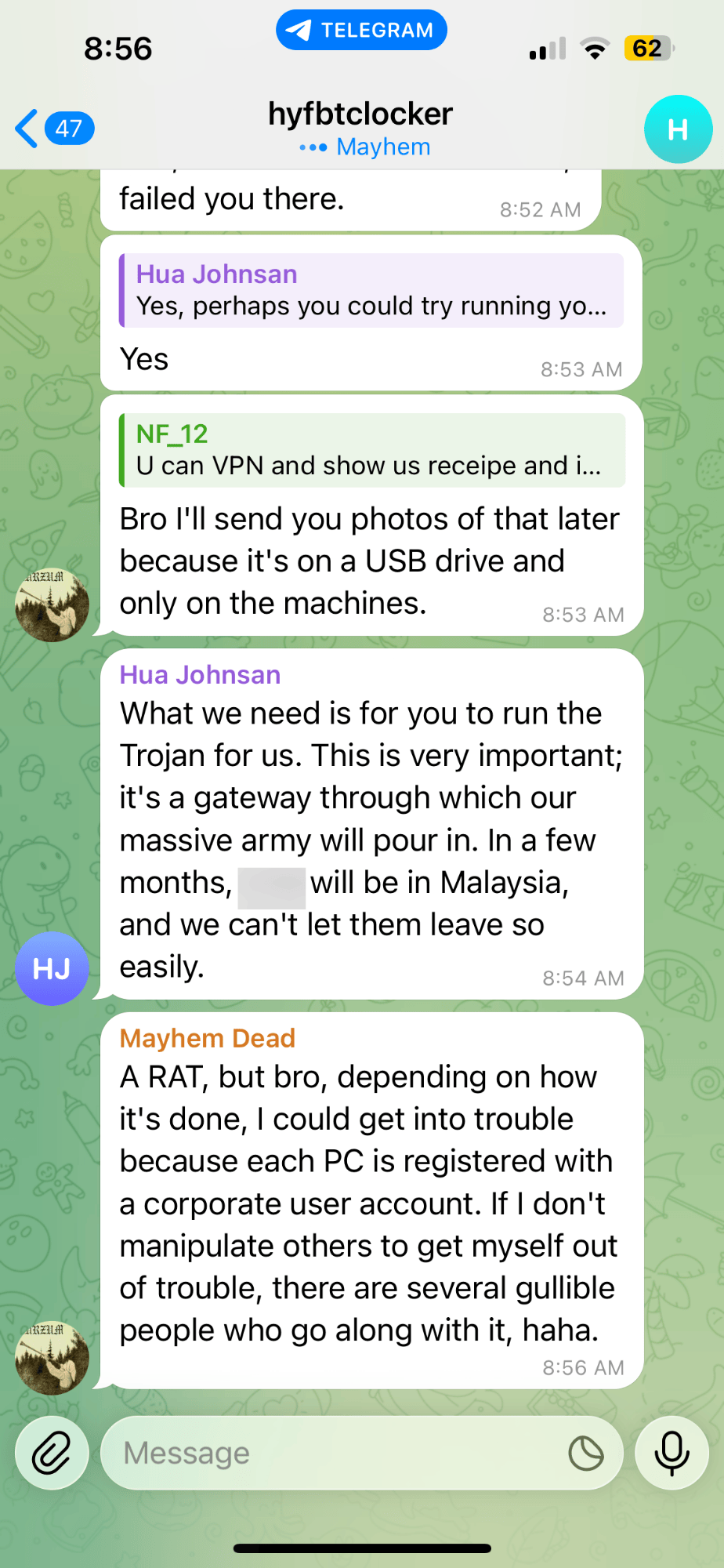
Insider Threat conversation on access and sensitive data
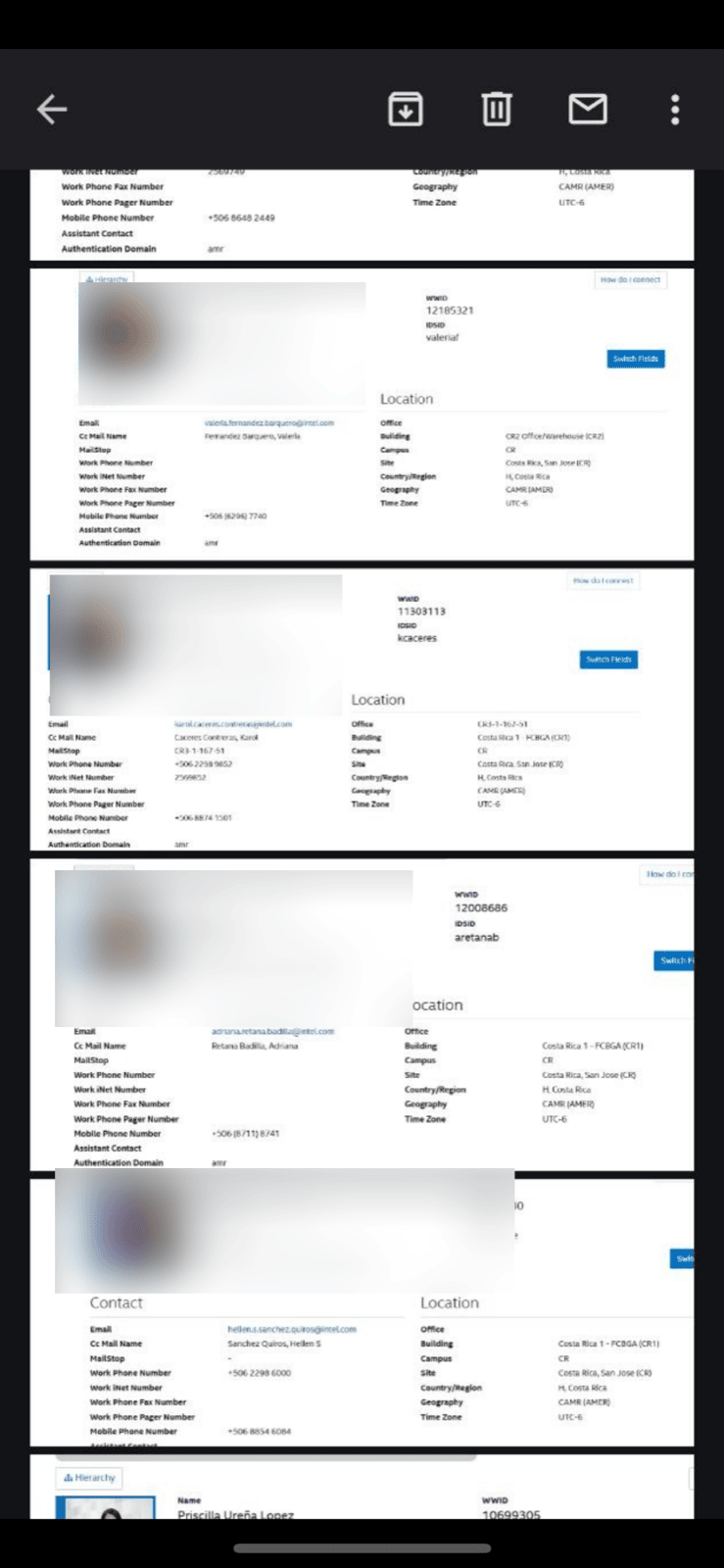
Insider Threat sample sensitive data
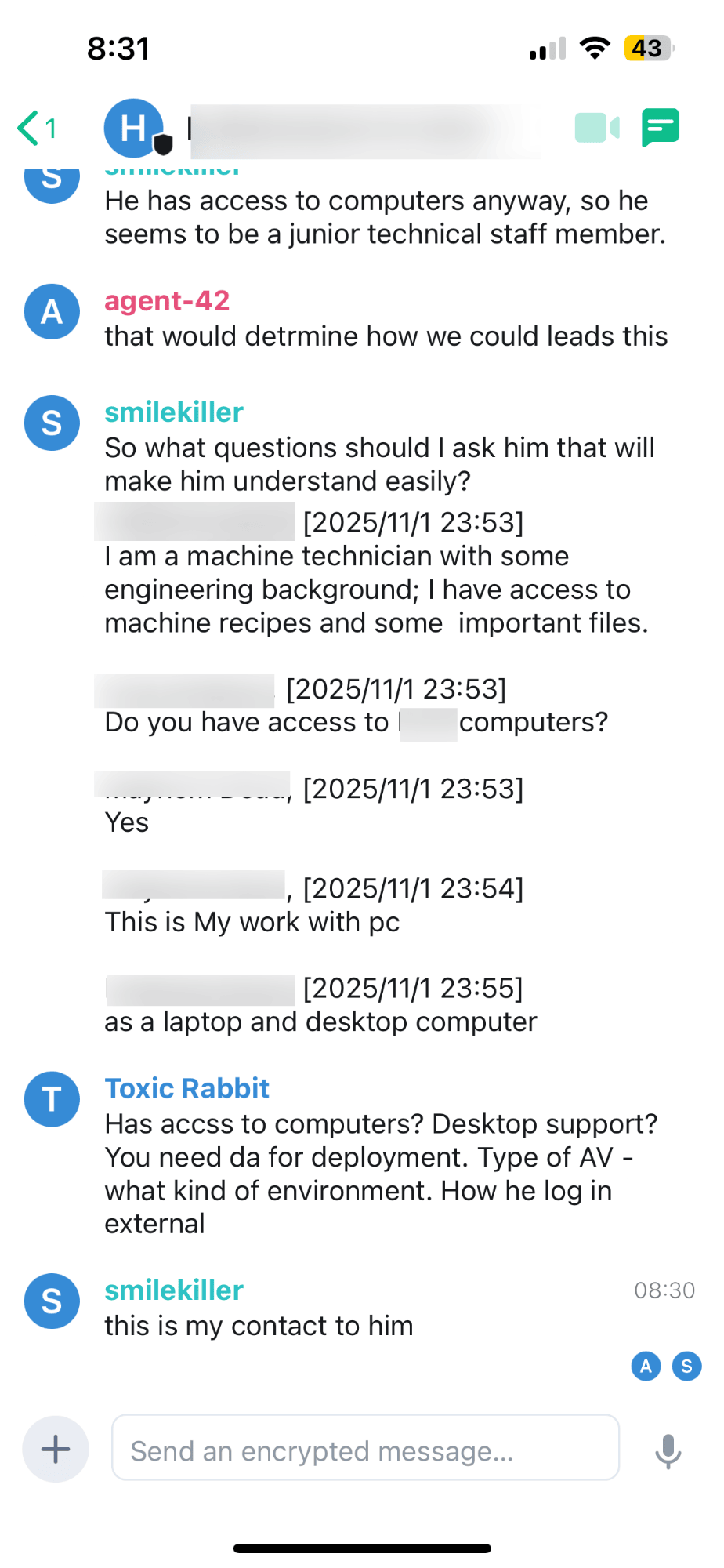
Insider Threat level of access conversation
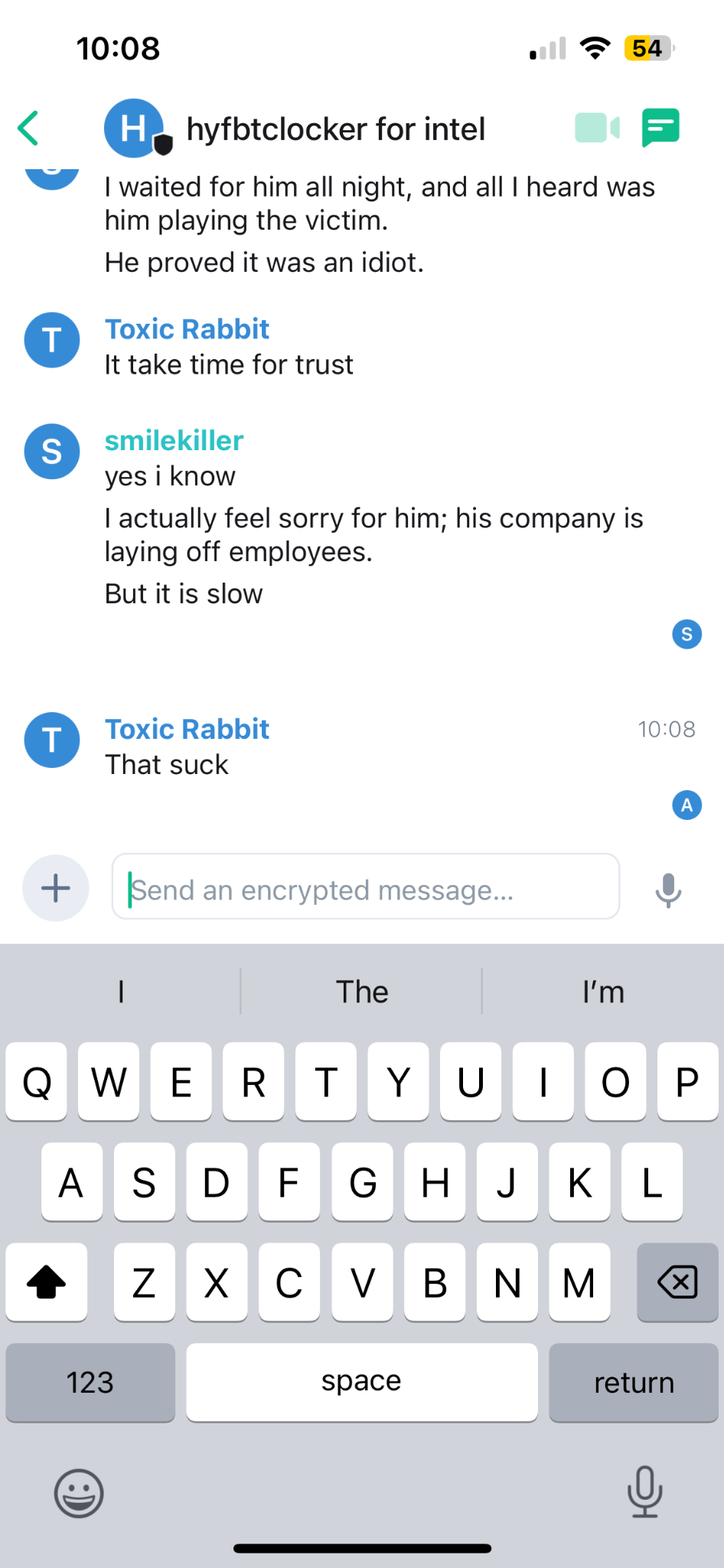
Insider Threat motive behind the attack.
Rather than existing in isolation, this example shows that ransomware intelligence can act as a controlled environment for studying insider-threat mechanics. The value lies in translating these observed behaviors into defensive awareness—helping organizations recognize how insider threats develop, evolve, and remain undetected long before overt harm occurs.
Intelligence Recipients & Where to Send Ransomware Intelligence
Once ransomware intelligence has been fully collected and packaged—including all supporting artifacts in a consolidated ZIP archive—it should be disseminated to the appropriate authorities and trusted partners. This ensures your findings support disruption efforts, victim assistance, and broader defensive awareness.
1. Federal & Law Enforcement Agencies
- FBI – Internet Crime Complaint Center (IC3): The primary federal intake point for ransomware intelligence.
- What to submit: Incident indicators, ransom notes, wallet addresses, and full SHADOW research packages.
- Portal: ic3.gov/Ransomware
- CISA (Cybersecurity and Infrastructure Security Agency): CISA utilizes this intelligence for national-level advisories and sector-wide defense.
- Coordination: cisa.gov/report
2. Sector-Specific & Peer Networks
- ISACs / ISAOs: Information Sharing & Analysis Centers provide a platform for distributing actionable intelligence to specific industries (e.g., MS-ISAC for local government, H-ISAC for healthcare).
- Ransom-ISAC: Of course the LOCK STAR initiative and our network of experts can provide insight with upcoming conferences and blogs, giving individuals and teams a platform to share their research.
- Trusted Communities: Private analyst exchanges allow for the rapid dissemination of indicators and lessons learned when shared within legal and ethical boundaries.
3. Stakeholder Alignment
- Legal & Insurance: Packaged intelligence supports claims processing, negotiation decisions, and regulatory compliance.
- Incident Response Providers: Sharing full packages enables IR teams to correlate findings across multiple campaigns and speed up detection for other victims.
Submission Best Practices
To ensure your intelligence is actionable and maintain its integrity, follow these standards:
- Provide Full Context: Submit complete ZIP archives rather than just text summaries.
- Apply Traffic Light Protocol (TLP): Clearly label the sensitivity of the data (e.g., TLP:AMBER or TLP:RED).
- Preserve Integrity: Maintain file hashes for all artifacts to ensure evidentiary value.
- Distinguish Data: Clearly separate objective facts (logs, chat screenshots) from analyst assessments.
- Coordinate Disclosure: Avoid public release until formal coordination with relevant agencies is complete.
The professional packaging and dissemination of intelligence represent the critical transition from passive observation to active disruption. By consolidating findings into a structured, actionable format for law enforcement and trusted partners, an analyst ensures that their efforts translate into tangible consequences for threat actors.
Operational Resilience & The "After-Action" Reset
Engaging with ransomware collectives and observing the exploitation of victims is a high-pressure, high-stakes endeavor. The SHADOW framework requires a degree of tactical empathy that can lead to "compassion fatigue" or psychological burnout if not managed carefully. There is a vast amount of darkness these groups will reveal, but there is a limit to how much an analyst can process before it begins to take a toll.
To maintain long-term operational effectiveness and mental well-being, analysts must prioritize Mindful Disconnection:
The Necessity of the "Escape"
Establishing a hard boundary between the digital underground and your personal life is not a luxury—it is a requirement for the mission.
- Physical Movement: Step away from the screen. A simple walk or physical exercise helps break the "tunnel vision" that often occurs during deep research.
- Sensory Grounding: Engage in activities that have nothing to do with technology. Spend time with family and friends to reconnect with the "human" world that exists outside of cybercrime.
- Controlled Escapism: Immerse yourself in a favorite show, book, or hobby. These "mindful moments" allow the brain to reset and flush out the persistent stressors of the dark web.
Mental Decontamination
Just as you would "wash" a piece of malware in a sandbox, you must "wash" your mind after a difficult engagement.
- Know Your Limit: Recognize the signs of burnout—cynicism, irritability, or obsession with the case.
- The Power of Disengagement: Understand that walking away from a conversation to preserve your mental health is a sign of a professional analyst, not a failure of the mission.
You cannot effectively defend others if you are compromised by the weight of the intelligence you gather. Protect your peace with the same rigor you use to protect your infrastructure.
Conclusion
The SHADOW framework is effective because it provides a structured, ethics-aligned method for understanding ransomware ecosystems without engaging in any operational behavior. Its value comes from how it reframes the study of threat groups: instead of focusing on individual incidents or technical IOCs, SHADOW emphasizes human dynamics, social signaling, and ecosystem behaviors.
Key strengths include:
1. Behavioral Insight Without Engagement
SHADOW prioritizes passive pattern recognition, allowing researchers to map:
- Recruitment norms
- Communication rituals
- Onboarding expectations
- Role hierarchies
- Trust mechanisms
This avoids direct participation while still producing meaningful intelligence.
2. Ethical HUMINT-Style Observation
By borrowing humane HUMINT principles—such as tactical empathy, detached observation, and contextual mapping—the framework supports ethical study of threat communities while reducing personal risk and legal ambiguity.
3. Cross-Persona Consistency
Synthetic personas, when used responsibly, allow researchers to test hypotheses:
- Which profiles are ignored?
- Which are approached?
- What reputational markers matter?
- How groups vet newcomers?
Patterns become visible across interactions rather than from any single data point.
4. Macro-Level Pattern Detection
SHADOW excels at extracting rhythms, not secrets:
- Typical recruitment cycles
- Standardized vetting questions
- Common reputational markers
- Cross-group cultural overlap
Ransom-ISAC's view
As someone who has spent time understanding the social behaviors of ransomware crews from a defensive and analytical viewpoint - SHADOW resonates because it mirrors real patterns seen in the field.
Here's what stands out:
1. Reputation Is Everything
Ransomware ecosystems function like underground businesses. Affiliates trust histories, signals, and persona consistencies far more than technical claims.
SHADOW captures this by emphasizing:
- Cross-context reputation
- Behavioral consistency
- Non-technical credibility signals
2. Most Groups Fail the Same Way
Internal fractures, trust breakdowns, unpaid affiliates, and poor leadership are often more damaging to groups than law enforcement pressure.
SHADOW's emphasis on operational rhythms makes these failures predictable.
3. People Behave Like People
Even in illicit ecosystems, the human element dominates:
- Ego
- Competition
- Status seeking
- Tribal identity
- Perceived fairness
SHADOW's psychology-aligned focus maps these patterns accurately.
4. Safe Distance Matters
The framework's passive, observational methodology reflects what seasoned analysts already practice:
maintain distance, never engage operationally, and extract insight from behavior—not participation. These insights help defenders anticipate—not react to—threat evolution.
Acknowledgements
Ransom-ISAC extends sincere thanks to all individuals and organizations who have reached out requesting assistance or sharing intelligence—your collaboration strengthens our collective defense against sophisticated threat actors and advances the broader cybersecurity community's understanding of evolving threats.
In memory of Brandon Meyer: A best friend, a mentor, and the inspiration behind my career in cybersecurity. His support guided me here, and his legacy continues through this work.